Researchers discovered two new vulnerabilities known as TPM-FAIL in Intel firmware-based TPM (fTPM) and STMicroelectronics' TPM chips that could be used by hackers to steal their targets' cryptographic keys.
TPM (short for Trusted Platform Module) is a chip used as a root of trust for a device's OS that can store highly sensitive data such as security keys, protecting them from malicious tools such as implanted rootkits or malware dropped by a threat actor.
TPMs can also be firmware-based solutions (fTPM) that run on separate 32-bit microcontrollers inside a CPU, as is the case of Intel processors starting with the Haswell generation (2013).
The two vulnerabilities allow hackers to circumvent this security shield and steal the data stored within a TPM. Once they have their hands on your signing keys, the attackers can forge digital signatures that can be used to tamper with the operating systems or to bypass authentication on the compromised machine.
TPM-FAIL attacks are practical
The TPM-FAIL side-channel attacks demonstrated by the researchers take advantage of a "leakage of the length of the nonce, which can easily be exploited using a lattice attack."
Timing leakage issues affect both Intel's firmware-based TPM (fTPM) and STMicroelectronics' TPM chip, with both platforms exhibiting flawed cryptographic signature generation with secret-dependent execution times.
While the sensitive information should never leave the TPM, the hackers are able to recover 256-bit private keys for ECDSA and ECSchnorr signatures from elliptic curves-based digital signature schemes as the research team from the Worcester Polytechnic Institute, the University of Lübeck, and the University of California, San Diego further discovered.
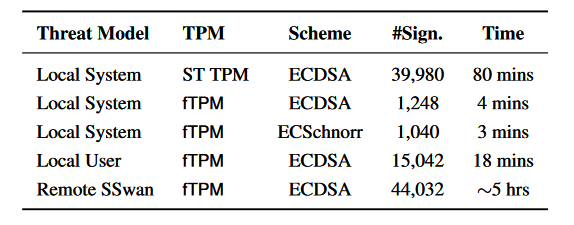
The attacks are practical seeing that, according to the researchers, "a local adversary can recover the ECDSA key from Intel fTPM in 4-20 minutes depending on the access level."
Attackers can also abuse TPM-FAIL vulnerable devices remotely on a fast network to recover the authentication key of a virtual private network (VPN) server in roughly five hours as demonstrated in the research.
The researchers were able to "recover ECDSA keys from an fTPM-endowed server runningStrongSwan VPN over a noisy network as measured by a client."
What devices are affected by TPM-FAIL
Most laptops, desktop, and server computers are vulnerable to TPM-FAIL attacks because they either use an Intel CPU with a firmware-based TPM (fTPM) or come with dedicated but unprotected TPM chips. However, TPM chips are also used for storing sensitive data by other computing devices like embedded devices and smartphones.
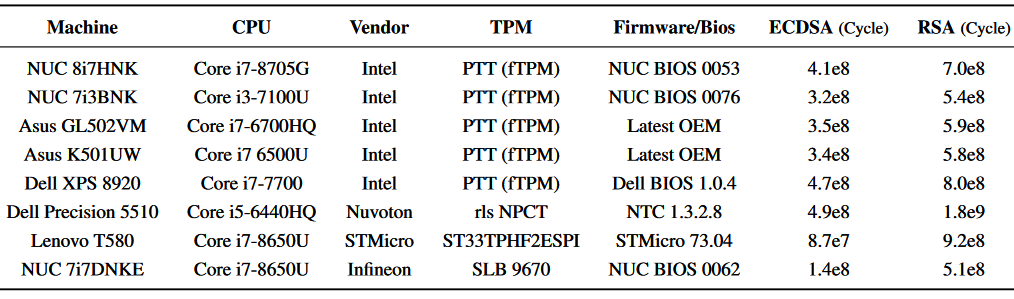
The vulnerable Intel fTPM, for instance, is used by the vast majority of computer manufacturers, including but not limited to Dell, HP, and Lenovo.
Also, numerous laptop manufacturers usually prefer to use the integrated Intel fTPM within CPUs rather than adding extra hardware, either for cutting down costs or based on trusting that Intel's fTPM will do a good job at protecting the users' information.
Last but not least, Intel's fTPM is also widely used by Intel Internet of Things (IoT) Platform family of products used in industry, healthcare, smart cities, and connected vehicles.
STMicroelectronics's ST33TPHF2ESPI TPM chip tested by the researchers is also a highly popular hardware solution used in personal computing devices, server platforms, and embedded systems.
TPM-FAIL vulnerabilities patched
Both companies issued patches for the TPM-FAIL vulnerabilities, either by releasing security patches or by issuing new TPM chips.
Intel upgraded their fTPM firmware to fix the security issue tracked as CVE-2019-11090 and STMicroelectronics issuing a new TPM chip to address the CVE-2019-16863 vulnerability, chips resistant against TPM-FAIL exploitation as the research team confirmed.
The researchers disclosed their findings to the Intel Product Security Incident ResponseTeam (iPSIRT) on February 1, 2019, which "issued a firmware update for Intel Manage-ment Engine (ME) including patches to address this issue on November 12, 2019."
STMicroelectronics was informed of the TPM chip flaw on May 15, 2019, and provided an updated ST33TPHF2ESPI TPM chip which was found to be resistant to TPM-FAIL attacks on September 12, 2019.
More information on these vulnerabilities is available in the TPM-FAIL: TPM meets Timing and Lattice Attacks technical paper.
The team behind TPM-FAIL will also present the research at the Real World Crypto 2020, New York (January 8-10, 2020) and the 29th USENIX Security Symposium, Boston (August 12-14, 2020).