Exploit for CrushFTP RCE chain released, patch now
A proof-of-concept exploit was publicly released for a critical remote code execution vulnerability in the CrushFTP enterprise suite, allowing unauthenticated attackers to access files on the server, execute code, and obtain plain-text passwords.
The vulnerability was discovered in August 2023, tracked as CVE-2023-43177, by Converge security researchers, who responsibly reported it to the vendor. The developers released a fix overnight in version CrushFTP 10.5.2.
Today, Converge published a proof-of-concept exploit for the CVE-2023-43177 flaw, making it critical for CrushFTP users to install the security updates as soon as possible.
Exploiting CrushFTP
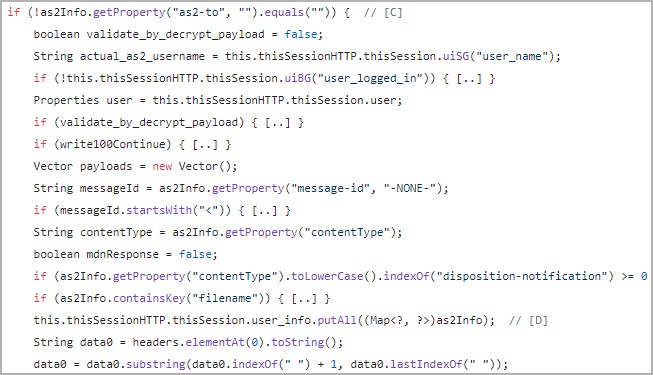
The CrushFTP exploit is conducted through an unauthenticated mass-assignment vulnerability, exploiting the AS2 header parsing to control user session properties.
This allows attackers to read and delete files, potentially leading to complete system control and root-level remote code execution.
The attackers can send payloads to the CrushFTP service on specific ports (80, 443, 8080, 9090) using web headers, which leave log traces.
Next, the attackers overwrite session data using Java's 'putAll()' function, enabling the impersonation of 'administrators,' and leverage the 'drain_log()' function to manipulate files as needed to maintain stealthiness.
Eventually, the attackers can leverage the 'sessions. obj' file in the program's installation folder to hijack live user sessions belonging to admin accounts, essentially achieving privileged escalation.
Having established admin access, the attacker can exploit flaws in the admin panel's handling of SQL driver loading and database configuration testing (testDB) to execute arbitrary Java code.
Converge has published a demonstration of the video of the PoC exploit in use, as shown below.
Thousands of vulnerable devices
According to Converge's report, there are roughly 10,000 public-facing CrushFTP instances and likely many more behind corporate firewalls. The attack surface is sizable even though the number of vulnerable instances hasn't been determined.
File transfer products like CrushFTP are particularly attractive to ransomware actors, specifically Clop, known for leveraging zero-day vulnerabilities in software like the MOVEit Transfer, GoAnywhere MFT, and Accelion FTA to conduct data theft attacks.
Unfortunately, the researchers revealed that even applying the patches doesn't secure CrushFTP endpoints against all possible threats.
"Converge's threat intelligence indicates that the security patch has been reverse-engineered, and adversaries have developed proofs of concepts. Because of that, upcoming exploitation is likely."
by Converge
To effectively mitigate the risk, it is recommended to follow these steps:
- Update CrushFTP to the latest version.
- Enable automatic security patch updates.
- Change the password algorithm to Argon.
- Audit for unauthorized users and check for recent password changes.
- Activate the new Limited Server mode for enhanced security.
Additional measures that can be implemented to enhance CrushFTP security further include:
- Using a limited privilege operating system service account for CrushFTP.
- Deploying Nginx or Apache as a reverse proxy for public-facing servers.
- Setting firewall rules to limit CrushFTP traffic to trusted IP ranges and hosts.
It's vital to implement these security measures as soon as possible, as the publicly disclosed exploit details of CVE-2023-43177 are likely to be used by hackers in opportunistic attacks.