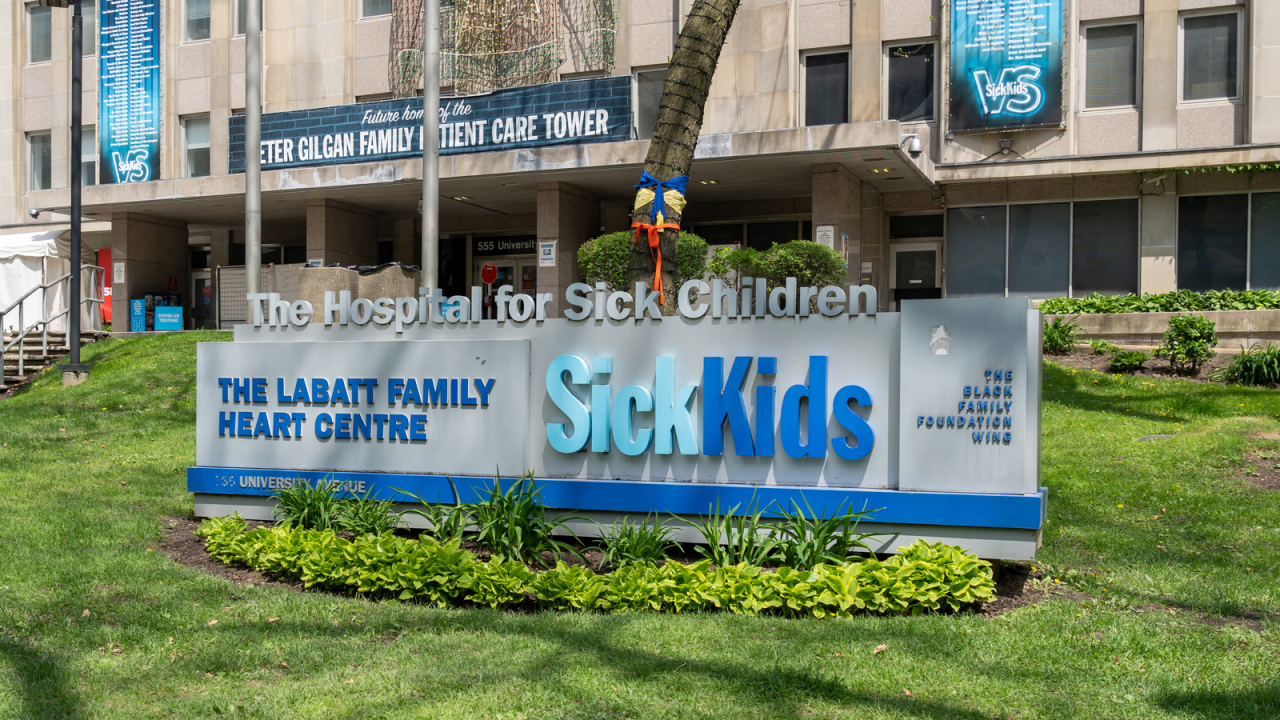Cisco is warning of five new Catalyst SD-WAN Manager products vulnerabilities with the most critical allowing unauthenticated remote access to the server.
Google has patched the fifth Chrome zero-day vulnerability exploited in attacks since the start of the year in emergency security updates released today.
Hackers are utilizing a new trick of using zero-point fonts in emails to make malicious emails appear as safely scanned by security tools in Microsoft Outlook.
The Hospital for Sick Children, more commonly known as SickKids, is among healthcare providers that were impacted by the recent breach at BORN Ontario.
TikTok is flooded with videos promoting fake nude celebrity photo leaks used to push referral rewards for the Temu online megastore.
U.S. educational nonprofit National Student Clearinghouse has disclosed a data breach affecting 890 schools using its services across the United States.
Credit reporting firm TransUnion has denied claims of a security breach after a threat actor known as USDoD leaked data allegedly stolen from the company's network. The Chicago-based company's over 10,000 employees provide their services to millions of consumers and more than 65,000 businesses from 30 countries. "Immediately upon discovering ...
The BlackCat (ALPHV) ransomware gang now uses stolen Microsoft accounts and the recently spotted Sphynx encryptor to encrypt targets' Azure cloud storage.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added to its catalog of known exploited vulnerabilities (KEV) a critical–severity issue tracked as CVE-2023-33246 that affects Apache's RocketMQ distributed messaging and streaming platform.
Citizen Lab says two zero-days fixed by Apple today in emergency security updates were actively abused as part of a zero-click exploit chain (dubbed BLASTPASS) to deploy NSO Group's Pegasus commercial spyware onto fully patched iPhones.
A new phishing campaign is abusing Microsoft Teams messages to send malicious attachments that install the DarkGate Loader malware.
Cisco is warning of a CVE-2023-20269 zero-day vulnerability in its Cisco Adaptive Security Appliance (ASA) and Cisco Firepower Threat Defense (FTD) that is actively exploited by ransomware operations to gain initial access to corporate networks.
Apple released emergency security updates to fix two new zero-day vulnerabilities exploited in attacks targeting iPhone and Mac users, for a total of 13 exploited zero-days patched since the start of the year.
Cybercriminals are leveraging a legitimate Windows tool called 'Advanced Installer' to infect the computers of graphic designers with cryptocurrency miners.
Johnson & Johnson Health Care Systems ("Janssen") has informed its CarePath customers that their sensitive information has been compromised in a third-party data breach involving IBM.
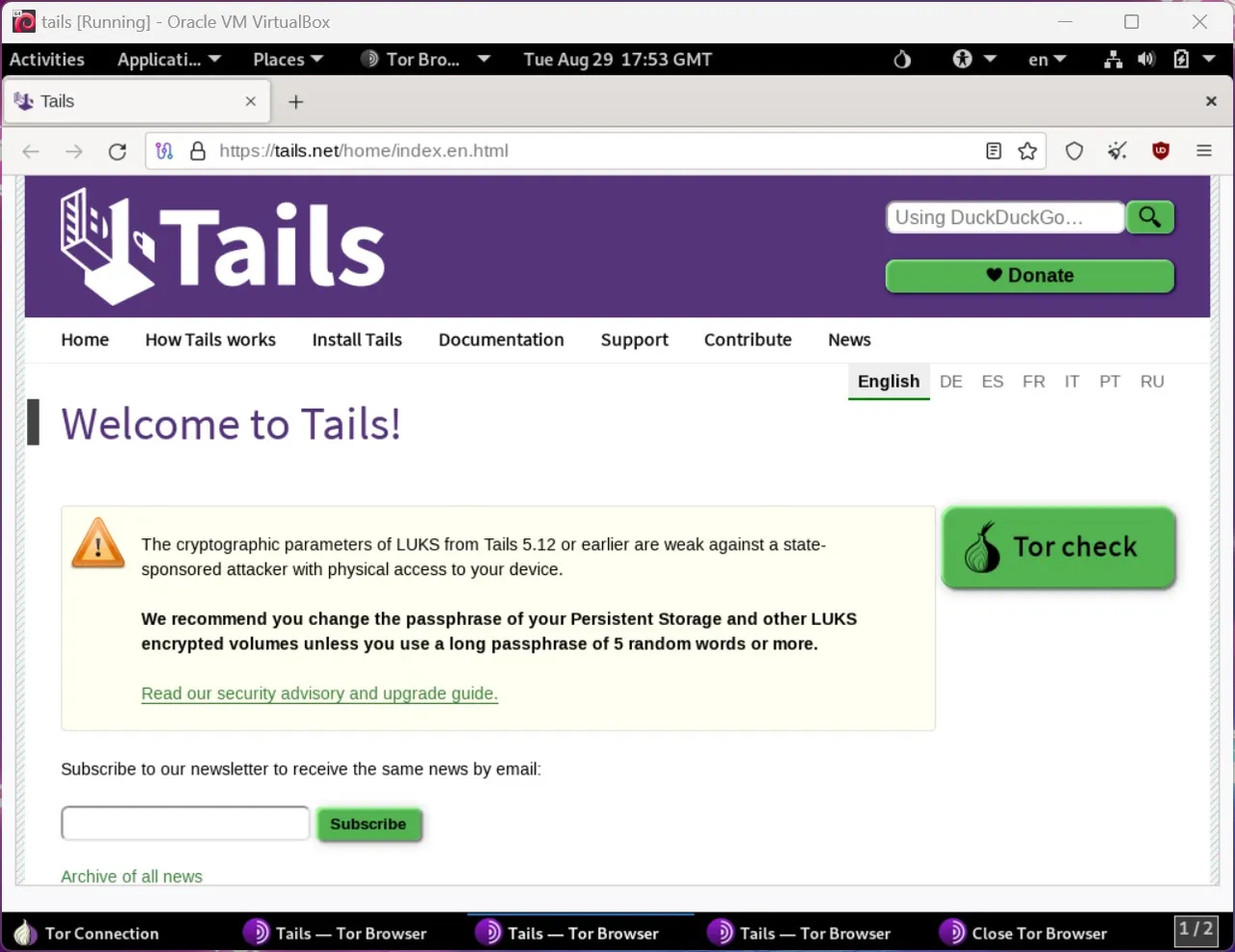
If you're looking for protection against surveillance and censorship, this Tor-based operating system is worth a try. Here's how you get started.
A team of researchers from the University of Wisconsin-Madison has uploaded to the Chrome Web Store a proof-of-concept extension that can steal plaintext passwords from a website's source code
A phishing campaign was observed predominantly targeting a notable energy company in the US, employing QR codes to slip malicious emails into inboxes and bypass security.
LinkedIn is being targeted in a wave of account hacks resulting in many accounts being locked out for security reasons or ultimately hijacked by attackers.