Change Healthcare lists the medical data stolen in ransomware attack
UnitedHealth has confirmed for the first time what types of medical and patient data were stolen in the massive Change Healthcare ransomware attack, stating that data breach notifications will be mailed in July.
On Thursday, the company published a data breach notification warning that the ransomware attack exposed a "substantial quantity of data" for a "substantial proportion of people in America."
While UnitedHealth has not explicitly shared how many people were affected, UnitedHealth CEO Andrew Witty stated during a congressional hearing that "maybe a third" of all American's health data was exposed in the attack.
According to the data breach notification, a massive trove of sensitive information was stolen, including:
- Health insurance information (such as primary, secondary or other health plans/policies, insurance companies, member/group ID numbers, and Medicaid-Medicare-government payor ID numbers);
- Health information (such as medical record numbers, providers, diagnoses, medicines, test results, images, care and treatment);
- Billing, claims and payment information (such as claim numbers, account numbers, billing codes, payment cards, financial and banking information, payments made, and balance due); and/or
- Other personal information such as Social Security numbers, driver's licenses or state ID numbers, or passport numbers.
However, Change Healthcare says that the exposed data may be different for each impacted individual and that patients' complete medical histories have not been seen in the stolen data.
"CHC is posting this substitute notice to provide customers and individuals with information about the criminal cyberattack on CHC systems and to share resources available to people who believe their personal data potentially being impacted," reads the Change Healthcare data breach notification.
"The review of personal information potentially involved in this incident is in its late stages. CHC is providing this notice now to help individuals understand what happened, let them know that their information may have been impacted, and give them information on steps they can take to protect their privacy, including enrolling in two years of complimentary credit monitoring and identity theft protection services if they believe that their information may have been impacted."
The company says it will begin mailing patients a formal data breach notification letter in late July but may not have mailing addresses for all those impacted.
In the meantime, those who are impacted can visit changecybersupport.com for more information on how to sign up for free credit monitoring and how the stolen data could be used in fraudulent activity.
The Change Healthcare ransomware attack
The data breach notifications are for a February ransomware attack on UnitedHealth subsidiary Change Healthcare when attackers stole 6 TB of data from the company.
The attack led to widespread outages in the US healthcare system, preventing doctors and pharmacies from filing claims. The disruption was particularly noticeable in pharmacies, which could not process any insurance claims or accept discount prescription cards, causing some patients to pay full price to receive medications.
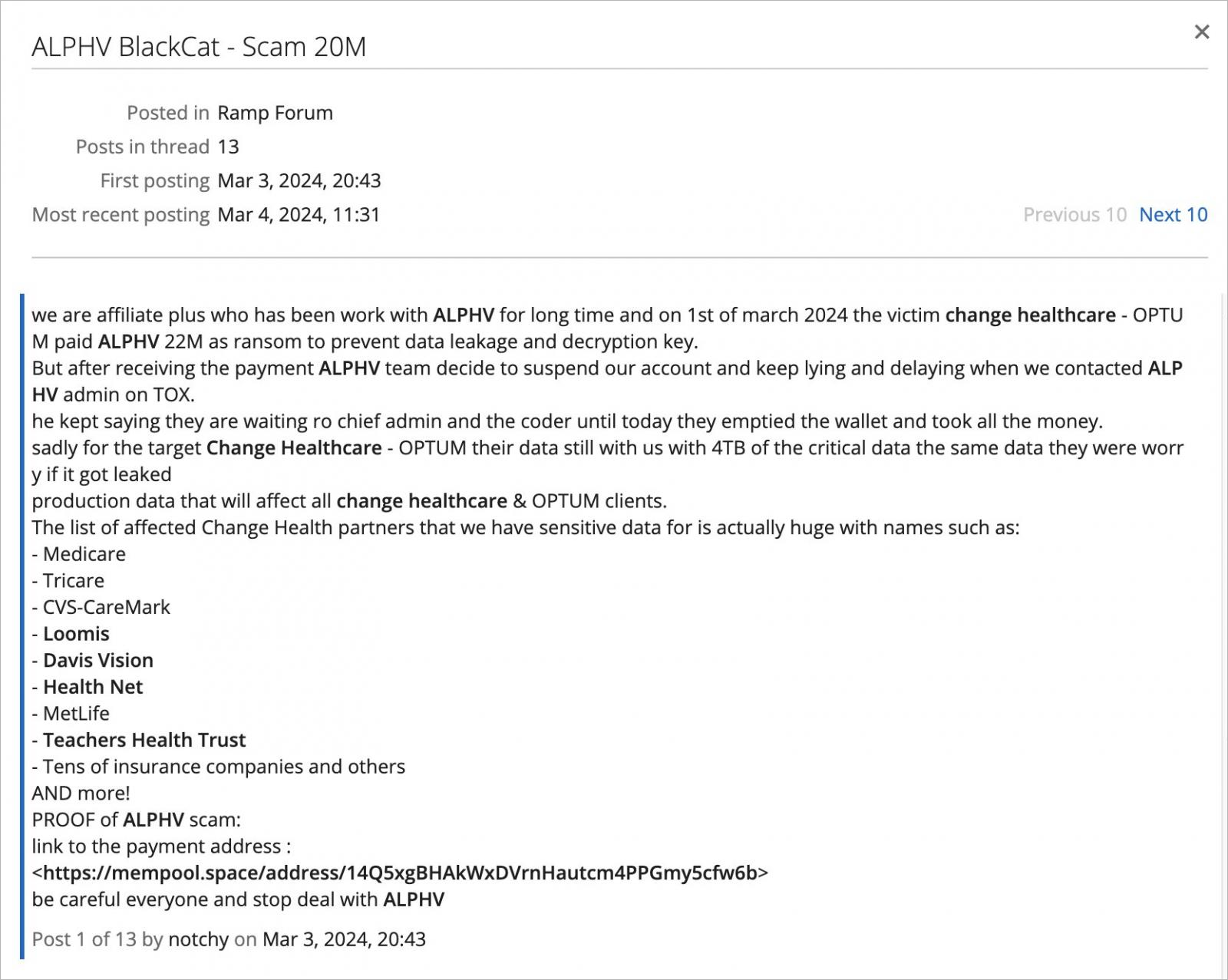
The BlackCat (aka ALPHV) ransomware gang conducted the attack, using stolen credentials to log into the company's Citrix remote access service, which did not have multi-factor authentication enabled.
UnitedHealth admitted to paying a ransom demand, allegedly $22 million, to the ransomware gang, which was supposed to be split with an affiliate who conducted the attack. However, the BlackCat operation instead shut down, stealing the entire payment for themselves.
The angry affiliate announced they still had Change Healthcare's data and did not delete it as promised. They then began leaking some of the stolen data on the RansomHub data leak site, demanding an additional payment for the data not to be released.
The entry for Change Healthcare mysteriously soon disappeared from the RansomHub website, indicating that United Health paid a second ransom demand.
United Health says that the Change Healthcare ransomware attack has caused $872 million in losses as of April, which will likely increase once all investigations and remediations have been completed.


Comments