DarkGate and Pikabot malware emerge as Qakbot’s successors
A sophisticated phishing campaign pushing the DarkGate malware infections has recently added the PikaBot malware into the mix, making it the most advanced phishing campaign since the Qakbot operation was dismantled.
The malicious email campaign started in September 2023, after the FBI seized and took down QBot's (Qakbot) infrastructure.
In a new report by Cofense, researchers explain that the DarkGate and Pikabot campaigns use tactics and techniques similar to previous Qakbot campaigns, indicating that the Qbot threat actors have now moved on to the newer malware botnets.
"This campaign is undoubtedly a high-level threat due to the tactics, techniques, and procedures (TTPs) that enable the phishing emails to reach intended targets as well as the advanced capabilities of the malware being delivered."
byCofense
As Qbot was one of the most pervasive malware botnets distributed through email, and both DarkGate and Pikabot are modular malware loaders with many of the same features as Qbot, this poses a dire risk to the enterprise.
Like Qbot, the the new malware loaders will be used by threat actors to gain initial access to networks and likely to perform ransomware, espionage, and data theft attacks.
The DarkGate and Pikabot campaign
Over the past Summer, there has been a massive increase in malicious emails pushing the DarkGate malware, with the threat actors switching to installing Pikabot as the primary payload in October 2023.
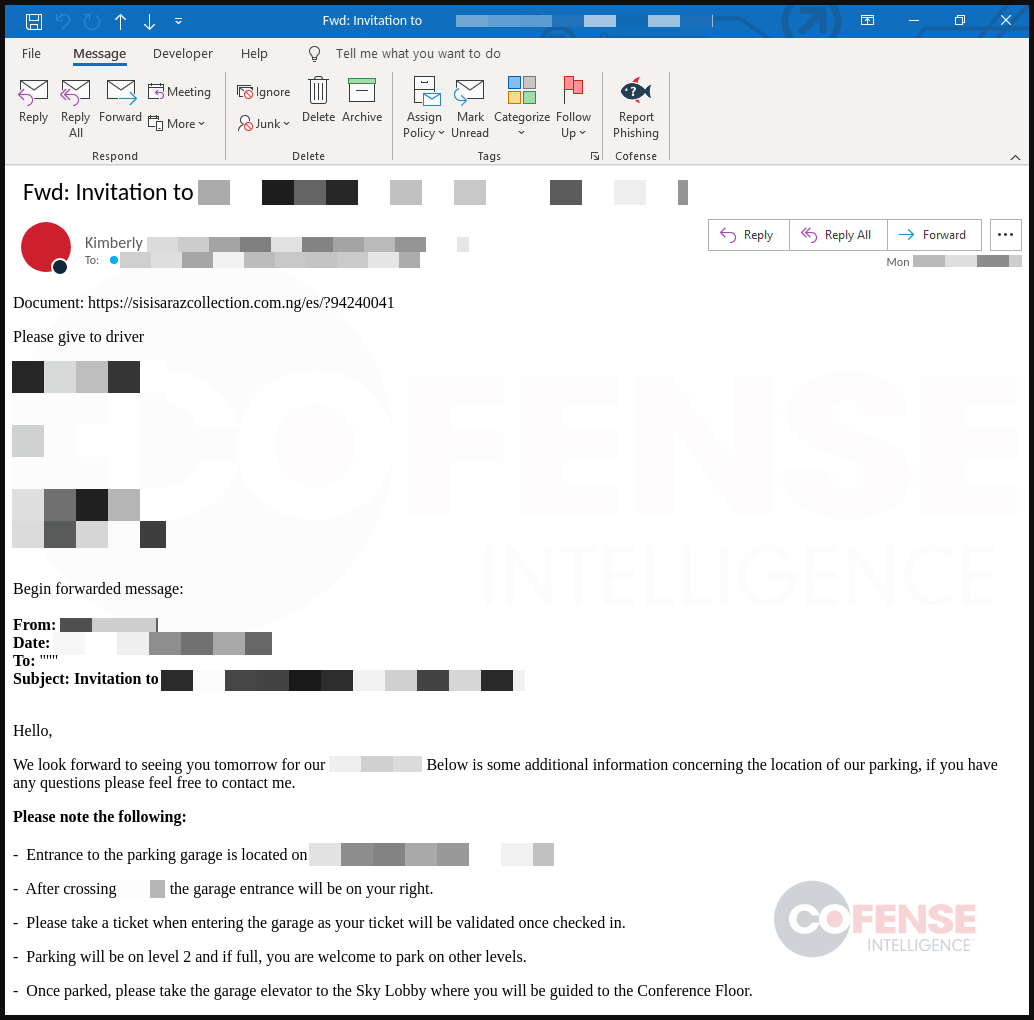
The phishing attack begins with an email that is a reply or forward of a stolen discussion thread, which increases the likelihood of the recipients treating the communication with trust.
Users clicking on the embedded URL go through a series of checks that verify they are valid targets and then prompt the target to download a ZIP archive containing a malware dropper that fetches the final payload from a remote resource.
Cofense reports that the attackers experimented with multiple initial malware droppers to determine which works the best, including:
- JavaScript dropper for downloading and executing PEs or DLLs.
- Excel-DNA loader based on an open-source project used for creating XLL files, exploited here for downloading and running malware.
- VBS (Virtual Basic Script) downloaders that can execute malware through .vbs files in Microsoft Office documents or invoke command-line executables.
- LNK downloaders that abuse Microsoft shortcut files (.lnk) to download and execute malware.
The final payload used in these attacks was the DarkGate malware through September 2023, which was replaced by PikaBot in October 2023.
DarkGate and PikaBot
DarkGate was first documented in 2017, but it only became available to the broader cybercrime community this past summer, resulting in a spike in its distribution through phishing and malvertising.
It is an advanced modular malware that supports a variety of malicious behaviors, including hVNC for remote access, cryptocurrency mining, reverse shell, keylogging, clipboard stealing, and information stealing (files, browser data).
PikaBot is a newer malware first seen in early 2023 that consists of a loader and a core module, incorporating extensive anti-debugging, anti-VM, and anti-emulation mechanisms.
The malware profiles infected systems and sends the data to its command and control (C2) infrastructure, awaiting further instructions.
The C2 sends commands instructing the malware to download and execute modules in the form of DLL or PE files, shellcode, or command-line commands, so it is a versatile tool.
Cofense warns that the PikaBot and DarkGate campaigns are run by knowledgeable threat actors whose abilities are above those of ordinary phishers, so organizations must familiarize themselves with the TTPs for this campaign.



Comments