Hackers use new Agent Raccoon malware to backdoor US targets
A novel malware named 'Agent Raccoon' (or Agent Racoon) is being used in cyberattacks against organizations in the United States, the Middle East, and Africa.
The attackers are believed to be nation-state threat actors discovered by Palo Alto Network's Unit 42, which reports seeing victims spanning various sectors, including government, telecommunications, education, real estate, retail, and non-profit organizations.
"We assess with medium confidence that this threat activity cluster aligns to nation-state related threat actors due to the nature of the organizations that were compromised, the TTPs observed and the customization of the tool set," explains the Unit 42 researchers.
"We have not confirmed a particular nation-state or threat group."
The selection of targets, nature of the deployed tools, data exfiltration methods, targeted intelligence, and the covert character of the attacks suggest that their goal is espionage.
Agent Raccoon backdoor
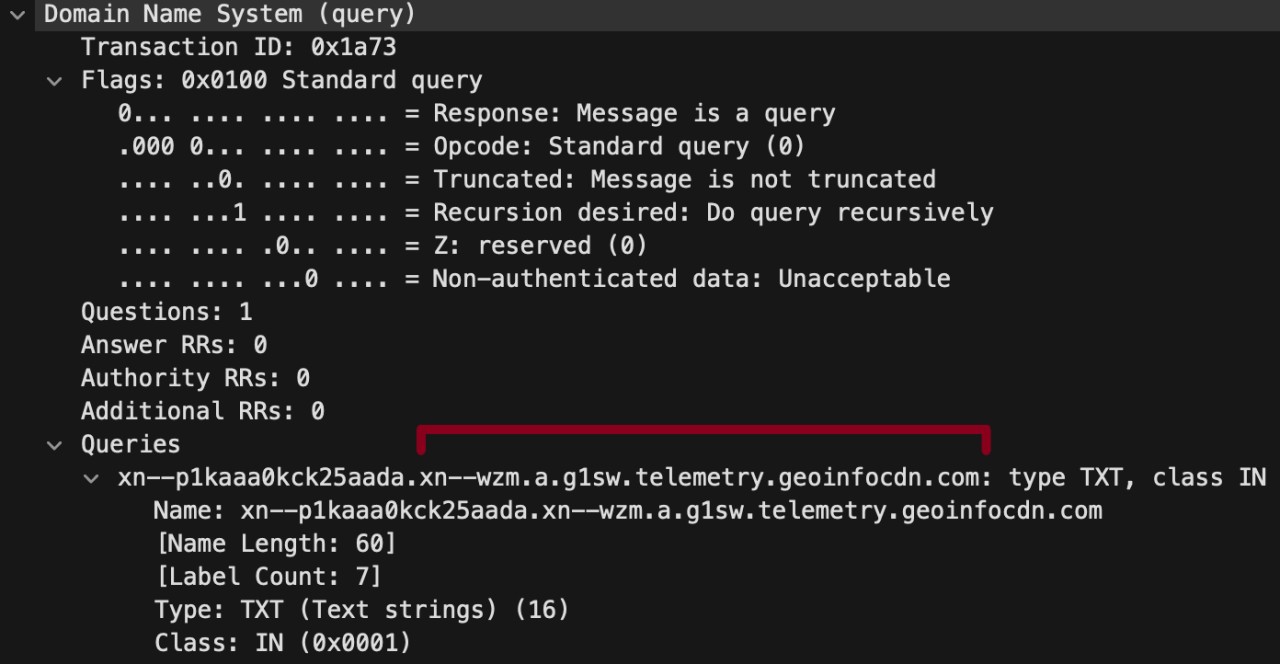
Agent Raccoon is a .NET malware disguised as a Google Update or Microsoft OneDrive Updater that leverages the DNS (Domain Name Service) protocol to establish a covert communication channel with the attackers' C2 (command and control) infrastructure.
The backdoor constructs queries with Punycode-encoded subdomains for evasion, while it also includes random values to make communications harder to track.
Unit 42 notes that while the malware itself lacks a persistence mechanism, their observations suggest that it is executed by scheduled tasks.
The malware is capable of remote command execution, file uploading and downloading, and providing remote access to the infected system.
The analysts also note that they have captured different samples of Agent Raccoon with slight code variations and optimizations in its settings, indicating that the malware's authors are actively developing and adapting it to specific operational requirements.
Other unique tools
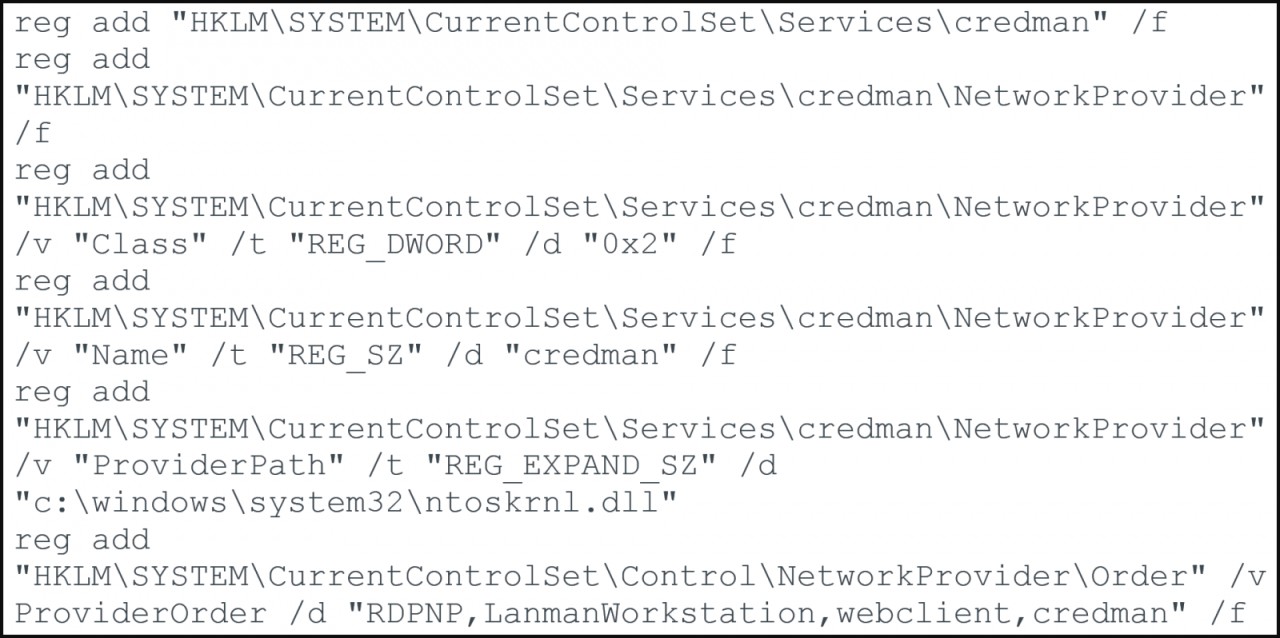
Apart from Agent Raccoon, the attackers also used a customized version of the Mimikatz credential dumping utility, named 'Mimilite,' and a DLL credential stealer mimicking the Windows Network Provider module, named 'Ntospy.'
Ntospy registers as a legitimate Network Provider module named "credman" to hijack the authentication process and capture user credentials, a well-documented attack method.
This tool, too, uses filenames that resemble Microsoft Update files and stores intercepted credentials in plaintext form locally on the breached device.
Finally, the attackers use PowerShell snap-ins to steal emails from Microsoft Exchange servers or steal victims' Roaming Profile folders, compressing the directory with 7-Zip for efficiency and stealth.
The observed email exfiltration process involved distinct search criteria for each inbox, indicating a targeted data harvesting approach that matches the presumed espionage operational profile.
The unknown activity cluster has notable overlaps with another threat actor that Unit 42 tracks as 'CL-STA-0043,' which is characterized as a nation-state threat actor with medium confidence.


Comments