Lazarus hackers target Windows IIS web servers for initial access

Lazarus is primarily financially motivated, with many analysts believing that the hackers' malicious activities help fund North Korea's weapons development programs. However, the group has also been involved in several espionage operations.
The latest tactic of targeting Windows IIS servers was discovered by South Korean researchers at the AhnLab Security Emergency Response Center (ASEC).
Attacks on IIS servers
Windows Internet Information Services (IIS) web servers are used by organizations of all sizes for hosting web content like sites, apps, and services, such as Microsoft Exchange's Outlook on the Web.
It is a flexible solution that has been available since the launch of Windows NT, supporting the HTTP, HTTPS, FTP, FTPS, SMTP, and NNTP protocols.
However, if the servers are poorly managed or outdated, they can act as network entry points for hackers.
Previously, Symantec reported about hackers deploying malware on IIS to execute commands on the breached systems via web requests, evading detection from security tools.
A separate report revealed that a hacking group named 'Cranfly' was employing an unknown technique of malware control by using IIS web server logs.
Lazarus' attacks on IIS
Lazarus first gains access to IIS servers using known vulnerabilities or misconfigurations that allow the threat actors to create files on the IIS server using the w3wp.exe process.
The hackers drop 'Wordconv.exe,' a legitimate file that is part of Microsoft Office, a malicious DLL ('msvcr100.dll') in the same folder, and an encoded file named 'msvcr100.dat.'
Upon launching 'Wordconv.exe,' the malicious code in the DLL loads to decrypt the Salsa20-encoded executable from msvcr100.dat and execute it in memory where antivirus tools can't detect it.
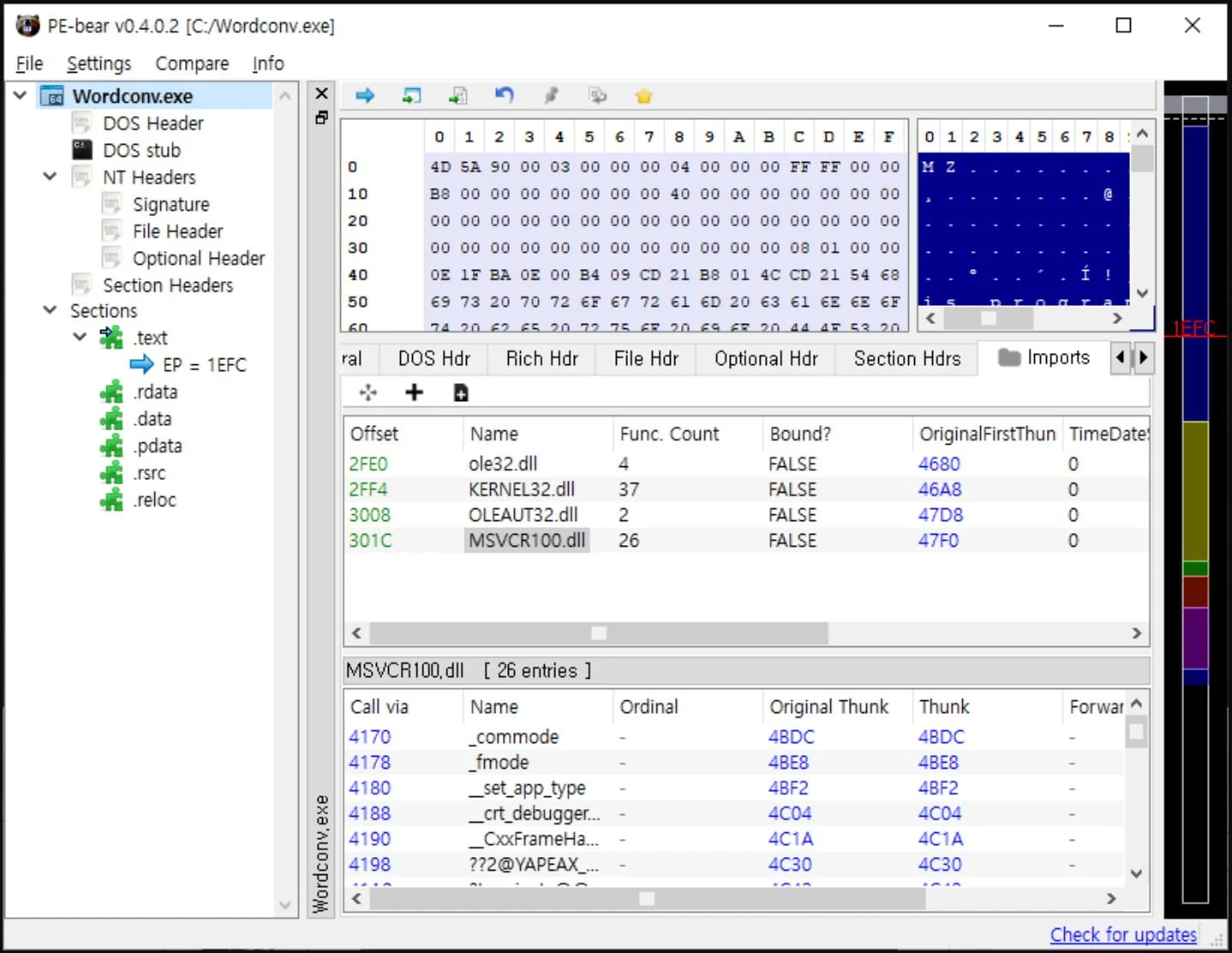
ASEC has found several code similarities between 'msvcr100.dll' and another malware it observed last year, 'cylvc.dll,' which was used by Lazarus to disable anti-malware programs using the "bring your own vulnerable driver" technique.
Hence, ASEC considers the newly discovered DLL file a new variant of the same malware.

In the second phase of the attack, Lazarus creates a second malware ('diagn.dll') by exploiting a Notepad++ plugin.
That second malware receives a new payload encoded with the RC6 algorithm this time, decrypts it using a hard-coded key, and executes it in memory for evasion.
ASEC could not determine what this payload did on the breached system, but it saw signs of LSASS dumping pointing to credential theft activity.
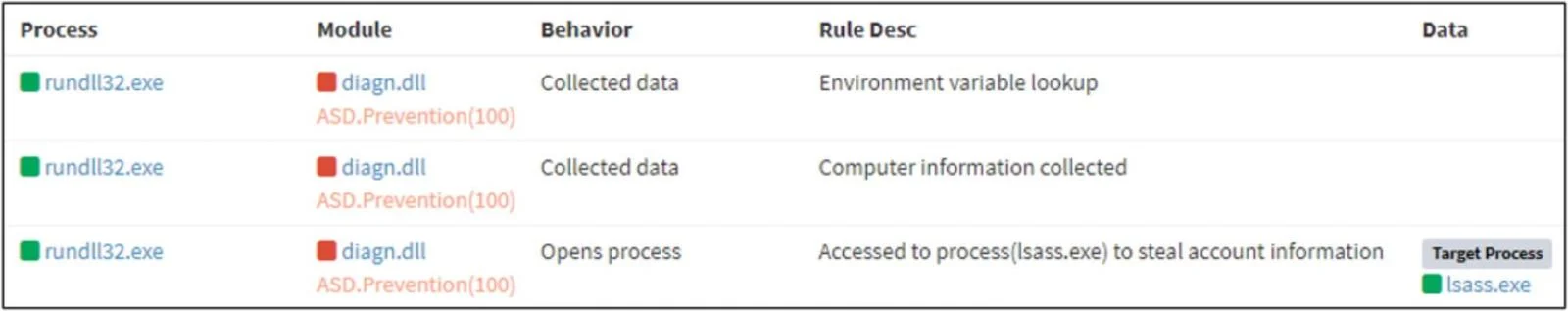
The final step of the Lazarus attack was to perform network reconnaissance and lateral movement through port 3389 (Remote Desktop) using valid user credentials, presumably stolen in the previous step.
However, ASEC has not uncovered any further malicious activities after the attackers spread laterally on the network.
As Lazarus is relying heavily on DLL sideloading as part of their attacks, ASEC recommends that organizations monitor for abnormal process execution.
"In particular, since the threat group primarily utilizes the DLL side-loading technique during their initial infiltrations, companies should proactively monitor abnormal process execution relationships and take preemptive measures to prevent the threat group from carrying out activities such as information exfiltration and lateral movement," concludes ASEC's report.

Comments