LogoFAIL attack can install UEFI bootkits through bootup logos
Multiple security vulnerabilities collectively named LogoFAIL affect image-parsing components in the UEFI code from various vendors. Researchers warn that they could be exploited to hijack the execution flow of the booting process and to deliver bootkits.
Because the issues are in the image parsing libraries, which vendors use to show logos during the booting routine, they have a broad impact and extend to x86 and ARM architectures.
According to researchers at firmware supply chain security platform Binarly, the branding has introduced unnecessary security risks, making it possible to execute malicious payloads by injecting image files in the EFI System Partition (ESP).
LogoFAIL discovery and impact
Abusing image parsers for attacks on the Unified Extensible Firmware Interface (UEFI) was demonstrated in 2009 when researchers Rafal Wojtczuk and Alexander Tereshkin presented how a BMP image parser bug could be exploited to infect the BIOS for malware persistence.
Discovering the LogoFAIL vulnerabilities started as a small research project on attack surfaces from image-parsing components in the context of custom or outdated parsing code in UEFI firmware.
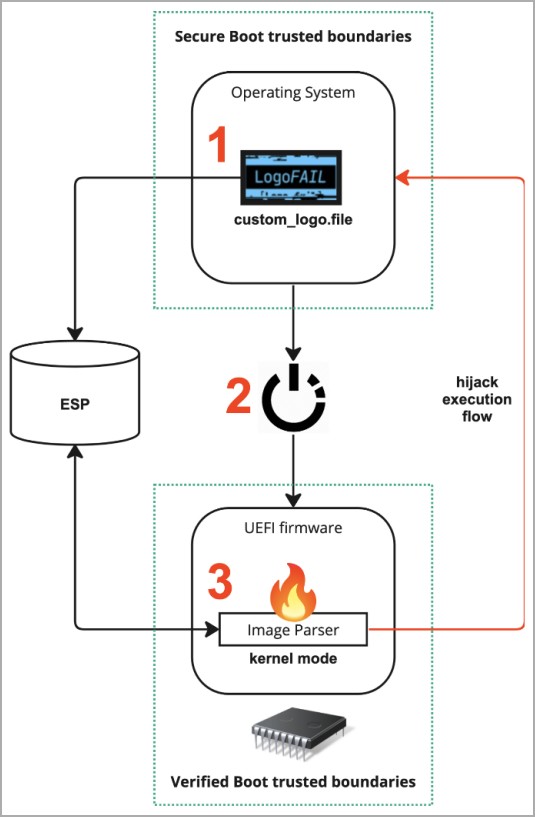
The researchers found that an attacker could store a malicious image or logo on the EFI System Partition (ESP) or in unsigned sections of a firmware update.
When these images are parsed during boot, the vulnerability can be triggered and an attacker-controlled payload can arbitrarily be executed to hijack the execution flow and bypass security features like Secure Boot, including hardware-based Verified Boot mechanisms (like Intel Boot Guard, AMD Hardware-Validated Boot or ARM TrustZone-based Secure Boot)"
by Binarly
Planting malware in such a way ensures persistence on the system that is virtually undetected, as illustrated in past attacks leveraging infected UEFI components [1, 2].
LogoFAIL does not affect runtime integrity because there is no need to modify the bootloader or the firmware, a method seen with the BootHole vulnerability or the BlackLotus bootkit.
In a video that Binarly shared privately, running the proof-of-concept (PoC) script and rebooting the device resulted in creating an arbitrary file on the system.
The researchers highlight that because it is not silicon-specific LogoFAIL vulnerabilities impact vendors and chips from multiple makers. The issues are present in products from many major device manufacturers that use UEFI firmware in consumer and enterprise-grade devices.
Binarly has already determined that hundreds of devices from Intel, Acer, Lenovo, and other vendors are potentially vulnerable, and so are the three major independent providers of custom UEFI firmware code: AMI, Insyde, and Phoenix.
However, it is also worth noting that the exact scope of the impact of LogoFAIL is still being determined.
"While we are still in the process of understanding the actual extent of LogoFAIL, we already found that hundreds of consumer- and enterprise-grade devices are possibly vulnerable to this novel attack," the researchers say.
The full technical details for LogoFAIL are to be presented on December 6 at the Black Hat Europe security conference in London.
According to the summary of the LogoFAIL presentation, the researchers disclosed their findings to multiple device vendors (Intel, Acer, Lenovo) and to the three major UEFI providers.


Comments