Microsoft drops SMB1 firewall rules in new Windows 11 build
Windows 11 will no longer add SMB1 Windows Defender Firewall rules when creating new SMB shares starting with today's Canary Channel Insider Preview Build 25992 build.
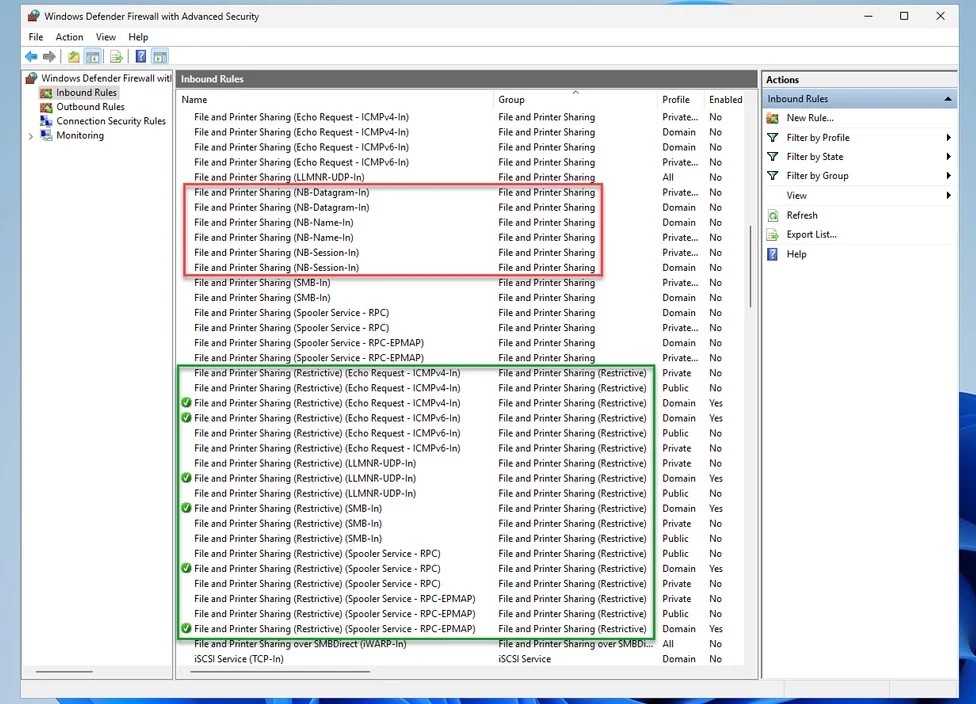
Before this change and since Windows XP SP2, creating SMB shares set up firewall rules automatically within the "File and Printer Sharing" group for the specified firewall profiles.
After today, Windows 11 will configure the updated "File and Printer Sharing (Restrictive)" group, omitting inbound NetBIOS ports 137-139 (which are SMB1 artifacts).
"This change enforces a higher degree of default of network security as well as bringing SMB firewall rules closer to the Windows Server "File Server" role behavior," Microsoft's Amanda Langowski and Brandon LeBlanc said.
"Administrators can still configure the "File and Printer Sharing" group if necessary as well as modify this new firewall group."
"We plan future updates for this rule to also remove inbound ICMP, LLMNR, and Spooler Service ports and restrict down to the SMB sharing-necessary ports only," added Microsoft Principal Program Manager Ned Pyle in a separate blog post.
The SMB client now also allows connections with an SMB server via TCP, QUIC, or RDMA over custom network ports different from the hardcoded defaults—previously, SMB only came with support for TCP/445, QUIC/443, and RDMA iWARP/5445.
Making Windows more secure, one step at a time
These improvements are part of an extensive effort to strengthen Windows and Windows Server security, as highlighted by other updates issued in recent months.
Following the introduction of Windows 11 Insider Preview Build 25982 in the Canary Channel, administrators can now enforce SMB client encryption for all outbound connections.
By requiring that all destination servers support SMB 3.x and encryption, Windows administrators can guarantee that all connections are secure, thus mitigating the risks of eavesdropping and interception attacks.
Admins can also configure Windows 11 systems to block sending NTLM data over SMB automatically on remote outbound connections to thwart pass-the-hash, NTLM relay, or password-cracking attacks, starting with the Windows 11 Insider Preview Build 25951.
These improvements are part of an extensive effort to strengthen Windows and Windows Server security, as highlighted by other updates issued in recent months.
Following the introduction of Windows 11 Insider Preview Build 25982 in the Canary Channel, administrators can now enforce SMB client encryption for all outbound connections.
By requiring that all destination servers support SMB 3.x and encryption, Windows administrators can guarantee that all connections are secure, thus mitigating the risks of eavesdropping and interception attacks.
Admins can also configure Windows 11 systems to block sending NTLM data over SMB automatically on remote outbound connections to thwart pass-the-hash, NTLM relay, or password-cracking attacks, starting with the Windows 11 Insider Preview Build 25951.


Comments