Microsoft Teams bug allows malware delivery from external accounts
Security researchers have found a simple way to deliver malware to an organization with Microsoft Teams, despite restrictions in the application for files from external sources.
With 280 million monthly active users, Microsoft Teams has been adopted by organizations as a communication and collaboration platform part of the Microsoft 365 cloud-based services.
Given the product's popularity with various organizations, Max Corbridge and Tom Ellson - members of the Red Team at UK-based security services company Jumpsec, poked around and discovered a way to deliver malware using Microsoft Teams with an account outside the target organization.
Attack details
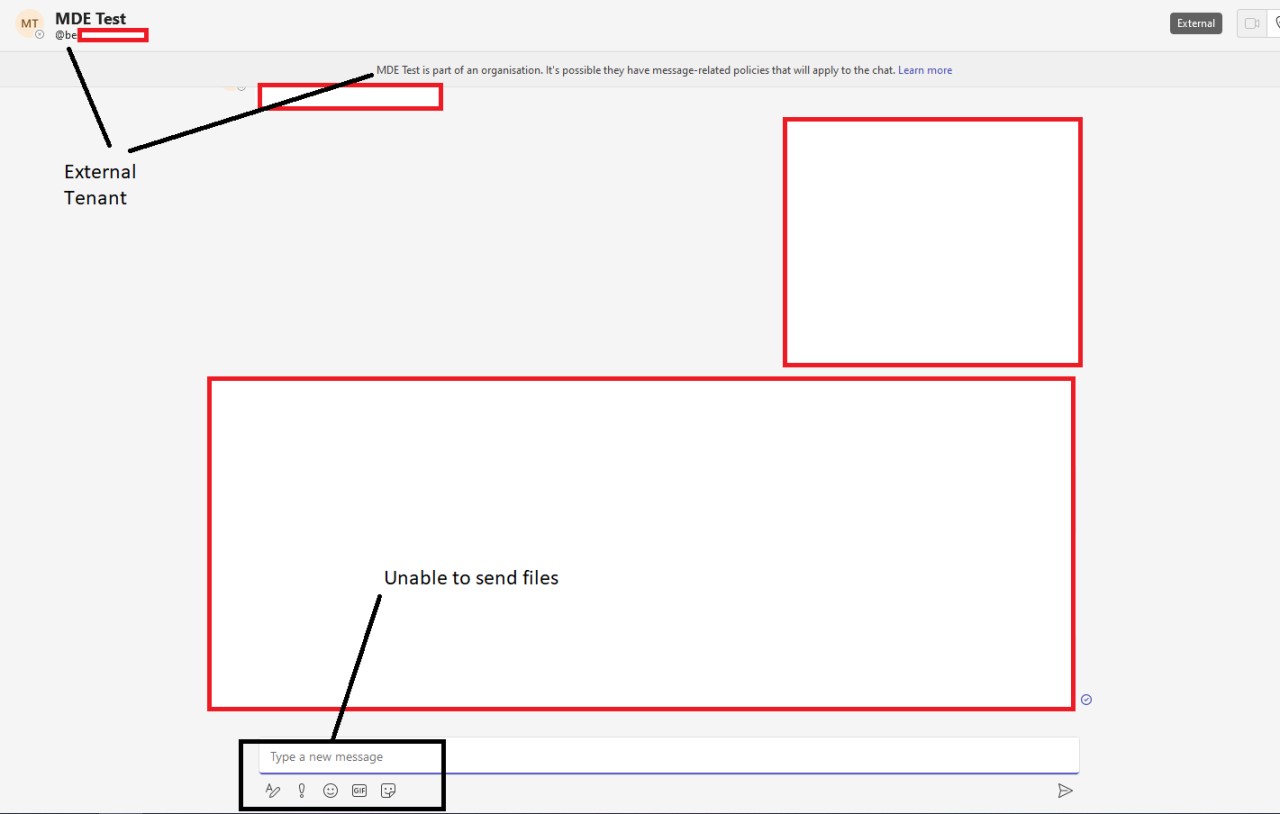
The attack works with Microsoft Teams running the default configuration, which permits communication with Microsoft Teams accounts outside the company, typically referred to as "external tenants."
Corbridge explains in a report that while this communication bridge would be enough for social engineering and phishing attacks, the method they found is more powerful as it allows sending a malicious payload directly to a target inbox.
Microsoft Teams has client-side protections in place to block file delivery from external tenant accounts.
However, the two Jumpsec Red Team members found that they could go around the restriction by changing the internal and external recipient ID in the POST request of a message, thus fooling the system into treating an external user as an internal one.
"When sending the payload like this, it is actually hosted on a Sharepoint domain and the target downloads it from there. It appears, however, in the target inbox as a file, not a link."
by Jumpsec Labs
The researchers tested the technique in the field and were able to successfully deliver a command and control payload into a target organizations inbox, as part of a covert red team engagement.
This attack bypasses existing security measures and anti-phishing training advice, giving attackers a fairly easy way to infect any organization using Microsoft Teams with its default configuration.
Furthermore, if the attacker registers a domain similar to the target organizations on Microsoft 365, their messages could be made to appear as if they come from someone inside the organization, and not an external tenant, thus increasing the likelihood of the target downloading the file.
Microsoft's response
The researchers reported their findings to Microsoft, assuming that the impact was significant enough to guarantee an immediate response from the tech giant.
Although Microsoft confirmed the existence of the flaw, the reply was that "it does not meet the bar for immediate servicing," meaning that the company does not see an urgency in fixing it.
BleepingComputer has also contacted Microsoft to ask when they plan to fix the issue and whether its severity has been reconsidered but we have not received a response by the time of publishing.
The recommended action for organizations that use Microsoft Teams and do not need to maintain regular communication with external tenants is to disable this feature from "Microsoft Teams Admin Center > External Access."
If external channels of communication need to be maintained, organizations can define specific domains in an allow-list, to lower the risk of exploitation.
Jumpsec's researchers also submitted a request to add external tenant-related events in the software's logging, which could help prevent attacks as they unfold, so vote this up if you want to contribute to pressing Microsoft to take action.



Comments