New Black Basta decryptor exploits ransomware flaw to recover files
Researchers have created a decryptor that exploits a flaw in Black Basta ransomware, allowing victims to recover their files for free.
The decryptor allows Black Basta victims from November 2022 to this month to potentially recover their files for free. However, it has been learned that the Black Basta developers fixed the bug in their encryption routine about a week ago, preventing this decryption technique from being used in newer attacks.
The Black Basta flaw
The 'Black Basta Buster' decryptor comes from Security Research Labs (SRLabs), which found a weakness in the encryption algorithm used by the ransomware gang's encryptors that allows for the discovery of the ChaCha keystream used to XOR encrypt a file.
"Our analysis suggests that files can be recovered if the plaintext of 64 encrypted bytes is known. Whether a file is fully or partially recoverable depends on the size of the file," explains the writeup on the method in SRLabs' GitHub repository.
"Files below the size of 5000 bytes cannot be recovered. For files between 5000 bytes and 1GB in size, full recovery is possible. For files larger than 1GB, the first 5000 bytes will be lost but the remainder can be recovered."
When Black Basta encrypts a file, it XORs the content using a 64-byte keystream created using the XChaCha20 algorithm. However, when using a stream cipher to encrypt a file whose bytes contain only zeros, the XOR key itself is written to the file, allowing retrieval of the encryption key.
Ransomware expert Michael Gillespie explained that Black Basta had a bug where they were reusing the same keystream during encryption, thus causing all 64-byte chunks of data containing only zeros to be converted to the 64-byte symmetric key. This key can then be extracted and used to decrypt the entire file.
This is illustrated by the image below, where two 64-byte chunks of 'zeros' were XORed and now contain the keystream used to encrypt the file.
While decrypting smaller files may not be possible, larger files like virtual machine disks can usually be decrypted, as they contain a large number of 'zero-byte' sections.
"Virtualised disk images, however, have a high chance of being recovered, because the actual partitions and their filesystems tend to start later," explains SRLabs.
"So, the ransomware destroyed the MBR or GPT partition table, but tools such as "testdisk" can often recover or re-generate those."
For files that do not contain large zero-byte chunks of data, SRLabs says it may still be possible to recover files if you have an older unencrypted version with similar data.
Some DFIR companies were aware of the flaw and had been utilizing it for months, decrypting their client's computers without having to pay a ransom.
The Black Basta Buster decryptor
The researchers at SRLabs have released a decryptor called Black Basta Buster that consists of a collection of python scripts that assist you in decrypting files under different scenarios.
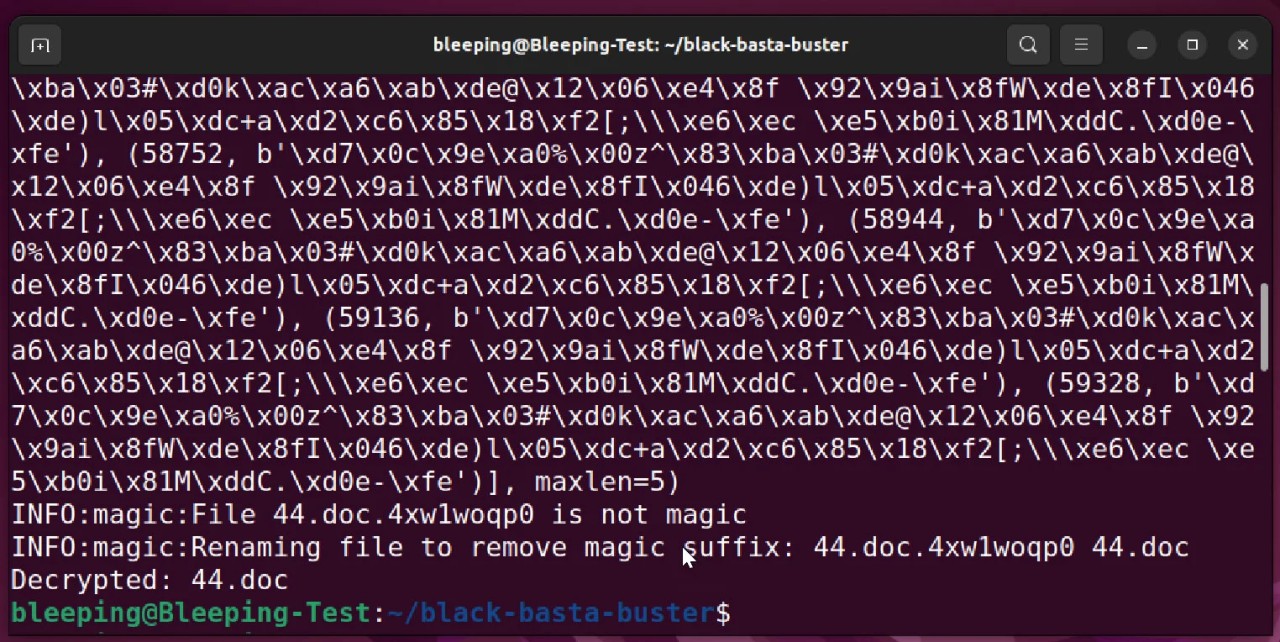
However, the researchers created a script called 'decryptauto.py' that attempts to perform automatic retrieval of the key and then use it to decrypt the file.
When we used the decryptauto.py script, it automatically retrieved the keystream and decrypted our file, as can be seen below.
However, as previously stated, this decryptor only works on Black Basta versions since November 2022 and up to a week ago. Furthermore, earlier versions that appended the .basta extension to encrypted files rather than a random file extension cannot be decrypted using this tool.
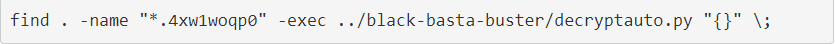
The decryptor only works on one file at a time, so if you wish to decrypt entire folders, you need to use a shell script or the 'find' command, as shown below. Just make sure to replace the extension and file paths as necessary.
While new Black Basta victims will no longer be able to recover their files for free, older victims may be more lucky if they were holding out for a decryptor.
Who is Black Basta?
The Black Basta ransomware gang launched its operation in April 2022 and became the newest cybercrime gang conducting double-extortion attacks on corporate victims.
By June 2022, Black Basta had partnered with the QBot malware operation (QakBot) to drop Cobalt Strike for remote access on corporate networks. Black Basta would then use these beacons to spread laterally to other devices on the network, steal data, and ultimately deploy encryptors.
Like other enterprise-targeting ransomware operations, Black Basta created a Linux encryptor to target VMware ESXi virtual machines running on Linux servers.
Researchers have also linked the ransomware gang to the FIN7 hacking group, a financially motivated cybercrime gang also known as Carbanak.
Since its launch, the threat actors have been responsible for a stream of attacks, including those on the Capita, American Dental Association, Sobeys, Knauf, and Yellow Pages Canada.
Recently, the ransomware operation attacked the Toronto Public Library, Canada's largest public library system.



Comments