New botnet malware exploits two zero-days to infect NVRs and routers
A new Mirai-based malware botnet named 'InfectedSlurs' has been exploiting two zero-day remote code execution (RCE) vulnerabilities to infect routers and video recorder (NVR) devices.
The malware hijacks the devices to make them part of its DDoS (distributed denial of service) swarm, presumably rented for profit.
The discovery of 'InfectedSlurs' comes from Akamai, who first spotted it on its honeypots in late October 2023. However, the botnet's initial activity dates back to late 2022.
The cybersecurity company reports that the impacted vendors haven't patched the two exploited flaws yet; hence, details about them have been reserved for now.
Discovery and targets
Akamai's Security Intelligence Response Team (SIRT) first discovered the botnet in October 2023, noticing unusual activity on a rarely used TCP port targeting their honeypots.
The activity concerned low-frequency probes attempting authentication via POST requests, followed by a command injection attempt.
Based on the data they held, SIRT analysts conducted an internet-wide scan and discovered that the targeted devices were linked to a specific NVR manufacturer, not named in the report for security reasons.
The botnet leverages an undocumented RCE flaw to gain unauthorized access to the device.
"The SIRT did a quick check for CVEs known to impact this vendor's NVR devices and was surprised to find that we were looking at a new zero-day exploit being actively leveraged in the wild," reads Akamai's report.
"Through the responsible disclosure process, the vendor communicated to us they are working on a fix that will likely be deployed in December 2023."
Further examination showed that the malware also uses default credentials documented in the vendor's manuals for multiple NVR products to install a bot client and perform other malicious activities.
popular among home users and hotels, which suffers from another zero-day RCE flaw leveraged by the malware.
The unnamed vendor of the router device promised to release security updates that address the problem in December 2023.
InfectedSlurs details
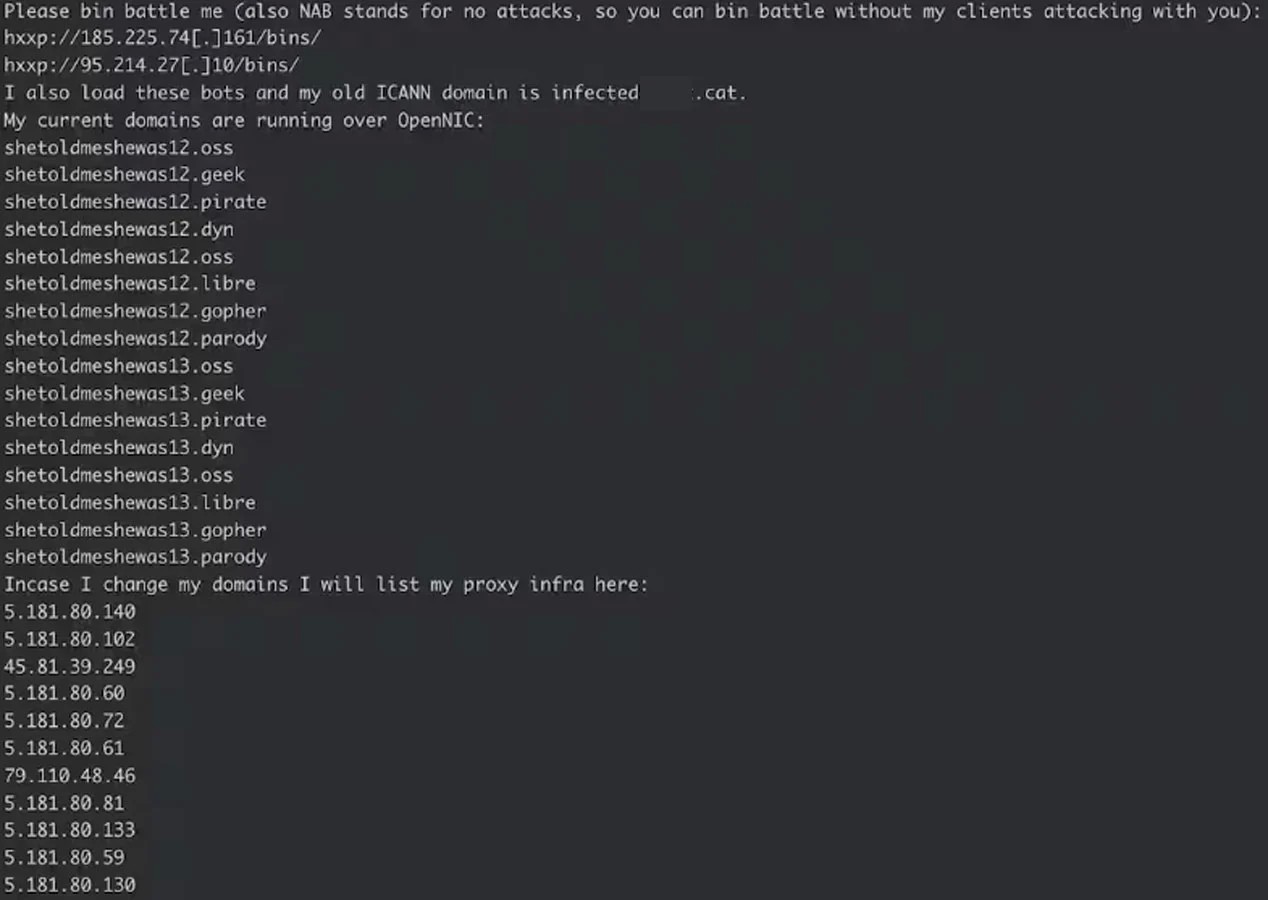
'InfectedSlurs,' named like that due to the use of offensive language in the C2 (command and control) domains and hardcoded strings, is a JenX Mirai variant.
Akamai reports that its C2 infrastructure is relatively concentrated and also appears to support hailBot operations.
Analysis revealed a now-deleted Telegram account linked to the cluster on Telegram.
The user also posted screenshots showing nearly ten thousand bots in the Telnet protocol and another 12,000 on specific device types/brands referred to as "Vacron," "ntel," and "UTT-Bots."
Akamai says that analysis of the bot samples it caught in October 2023 shows little code modifications compared to the original Mirai botnet, so it's a self-propagating DDoS tool supporting attacks using SYN, UDP, and HTTP GET request floods.
Like Mirai, InfectedSlurs doesn't include a persistence mechanism. Given the lack of a patch for the affected devices, rebooting your NVR and router devices should temporarily disrupt the botnet.

Comments