New Microsoft Azure AD CTS feature can be abused for lateral movement
Microsoft's new Azure Active Directory Cross-Tenant Synchronization (CTS) feature, introduced in June 2023, has created a new potential attack surface that might allow threat actors to more easily spread laterally to other Azure tenants.
Microsoft tenants are client organizations or sub-organizations in Azure Active Directory that are configured with their own policies, users, and settings.
However, as large organizations may be split up into multiple tenants for organizational purposes, it may sometimes be easier to allow users to synchronize between authorized tenants controlled by the same entity.
In June, Microsoft introduced a new Cross-Tenant Synchronization (CTS) feature that allows an administrator to synchronize users and groups across multiple tenants and tenant resources, offering seamless collaboration, automating lifecycle management of B2B projects, etc.
When configuring CTS, an Azure 'source' tenant will be synchronized with a 'target' tenant, where users from the source can automatically be synchronized to the target tenant. When synchronizing users, the user is only pushed from the source and not pulled from the target, making this a one-sided synchronization.
However, if improperly configured, attackers who have already compromised a tenant and gained elevated privileges may exploit the new feature to move laterally to other connected tenants and then deploy rogue CTS configurations to establish persistence on those networks.
This attack surface was previously described by Invictus, whose report primarily focuses on detecting threat actors abusing this feature.
CTS configuration gaps
In a report published yesterday, cybersecurity firm Vectra AI elaborates on how threat actors can abuse this feature to spread laterally to linked tenants or even use this feature for persistence.
However, they also warn that abusing this feature requires a threat actor to first compromise a privileged account or gain privilege escalation in a breached Microsoft cloud environment.
"We have not observed the use of this technique in the wild, but given the historical abuse of similar functionality — we present details for defenders to understand how the attack would present and how to monitor for its execution," Vectra AI explains in their report.
The first technique described in Vectra AI's report involves reviewing the CTS configurations to identify target tenants connected through these policies and, specifically, look for tenants with 'Outbound Sync' enabled, which allows syncing to other tenants.
Upon finding a tenant that meets those criteria, the attacker locates the app used for CTS syncing and modifies its configuration to add the compromised user into its sync scope, gaining access to the other tenant's network. This allows the threat actor to achieve lateral movement without requiring new user credentials.
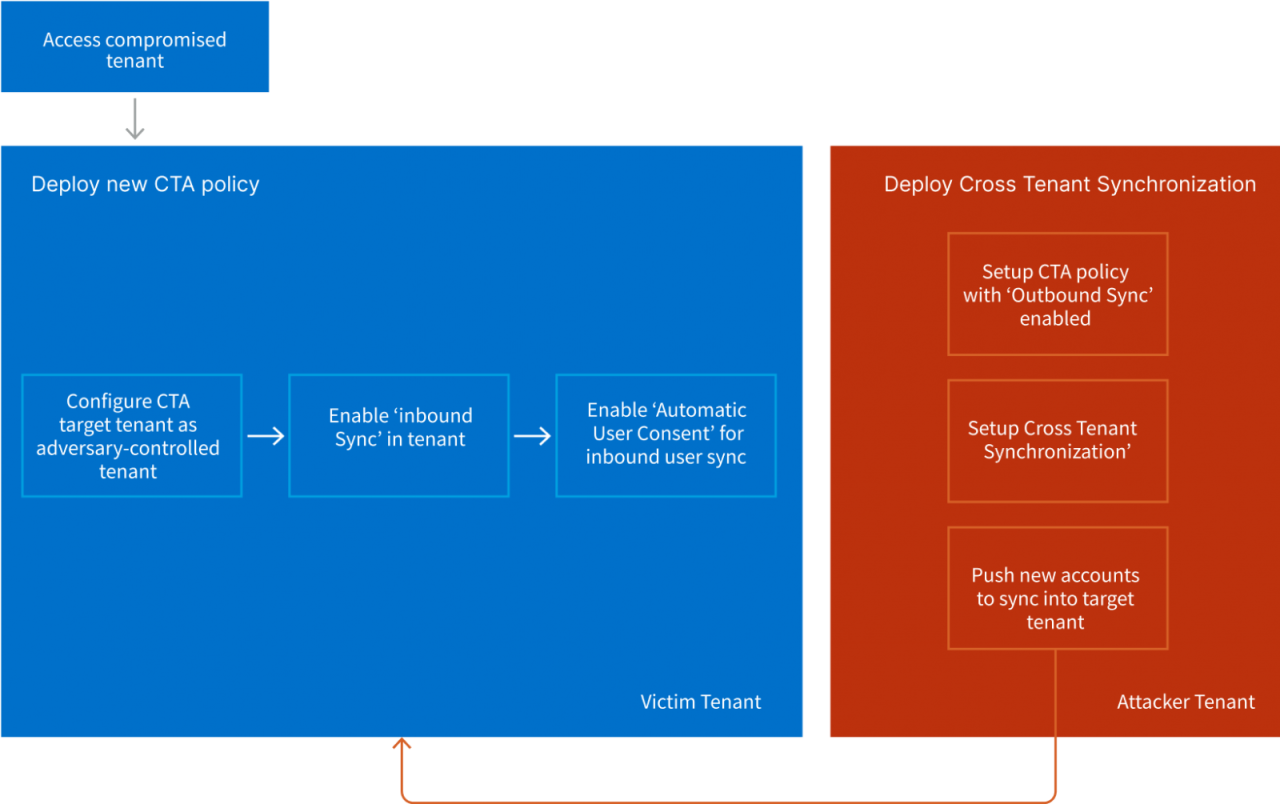
The second technique presented by Vectra involves deploying a rogue CTS configuration to maintain persistent access to the target tenants. Once again, it needs to be noted that this method requires a threat actor to already compromise a privileged account in the tenant.
Specifically, the attacker deploys a new CTS policy and enables 'Inbound Sync' and 'Automatic User Consent,' allowing them to push new users from their external tenant to the target anytime.
This setup grants the attacker access to the target tenant anytime via the external account.
Even if the rogue accounts are removed, the attacker can create and "push" new users at will, gaining immediate access to the resources of the target tenant, hence why the researchers calls this a "backdoor."
Defending against these attacks
While no known attacks have abused this feature, the researchers have offered guidance on hardening your configuration to prevent the feature from being abused.
Vectra proposes that CTS target tenants must avoid implementing a default or overly inclusive inbound CTA configuration and, if possible, set limits on which users and groups can access their cloud environments.
CTS source tenants that act as the initial breach points must monitor all privileged users for suspicious activity.
Invictus' report provides detailed information on how CTS activity is logged, allowing admins to detect malicious behavior.
BleepingComputer contacted Microsoft with questions on the report, but they declined to comment.



Comments