New NKAbuse malware abuses NKN blockchain for stealthy comms
A new Go-based multi-platform malware identified as 'NKAbuse' is the first malware abusing NKN (New Kind of Network) technology for data exchange, making it a stealthy threat.
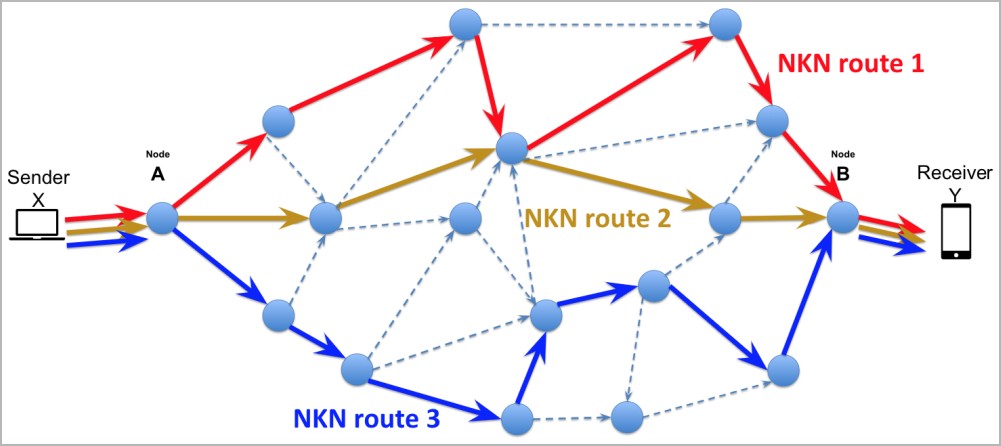
NKN is a relatively new decentralized peer-to-peer network protocol leveraging blockchain technology to manage resources and maintain a secure and transparent model for network operations.
One of the goals of NKN is to optimize data transmission speed and latency across the network, which is achievable by calculating efficient data packet travel paths.
Individuals can participate in the NKN network by running nodes, similar to the Tor network, and currently, there are approximately 60,710 nodes in it.
This relatively large number of nodes contributes to robustness, decentralization, and ability to handle significantly high volumes of data.
NKAbuse details
Kaspersky reports the discovery of a novel malware named NKAbuse, which primarily targets Linux desktops in Mexico, Colombia, and Vietnam.
One NKAbuse infection spotted by Kaspersky involves the exploitation of an old Apache Struts flaw (CVE-2017-5638) to attack a financial company.
Although most attacks target Linux computers, the malware can compromise IoTs and supports MIPS, ARM, and 386 architectures.
NKAbuse abuses NKN to launch DDoS (distributed denial of service) attacks that are hard to trace back to a specific infrastructure and unlikely to be flagged due to originating from a novel protocol not actively monitored by most security tools.
"This threat (ab)uses the NKN public blockchain protocol to carry out a large set of flooding attacks and act as a backdoor inside Linux systems." explains Kaspersky
Specifically, the malware client communicates with the bot master through NKN to send and receive data. At the same time, its ability to keep multiple concurrent channels alive gives resilience to its communication line.
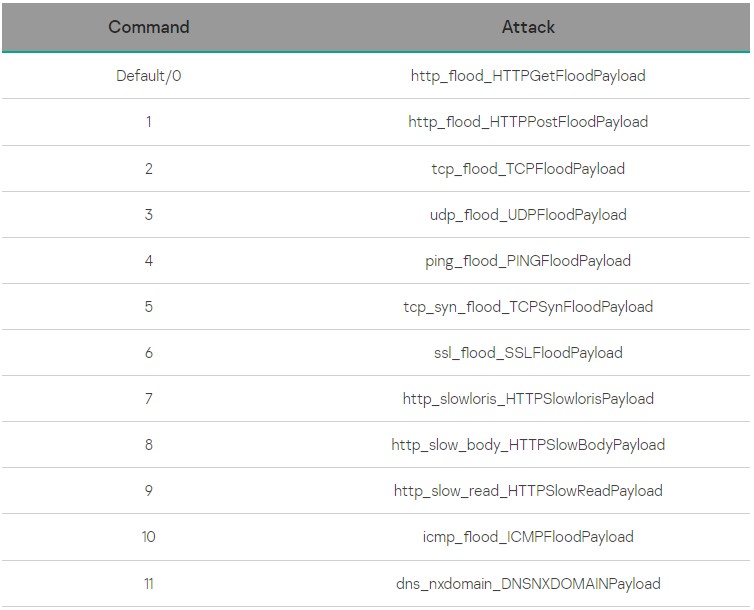
The payload commands sent by the C2 include HTTP, TCP, UDP, PING, ICMP, and SSL flood attacks aimed at a specified target.
"All these payloads historically have been used by botnets, so, when combined with the NKN as the communication protocol, the malware can asynchronously wait for the master to launch a combined attack," Kaspersky says.
In addition to the DDoS capabilities, NKAbuse also acts as a remote access trojan (RAT) on compromised systems, allowing its operators to perform command execution, data exfiltration, and snap screenshots.
This plethora of capabilities that make NKAbuse highly versatile and adaptive isn't typical in the DDoS botnet space.
Additionally, using blockchain technology that guarantees availability and obfuscates the source of the attacks makes defending against this threat very challenging.



Comments