Okta warns of "unprecedented" credential stuffing attacks on customers
Okta warns of an "unprecedented" spike in credential stuffing attacks targeting its identity and access management solutions, with some customer accounts breached in the attacks.
Threat actors use credential stuffing to compromise user accounts by trying out in an automated manner lists of usernames and passwords typically purchased from cybercriminals.
In an advisory today, Okta says the attacks seem to originate from the same infrastructure used in the brute-force and password-spraying attacks previously reported by Cisco Talos.
In all attacks that Okta observed the requests came through the TOR anonymization network and various residential proxies (e.g. NSOCKS, Luminati, and DataImpulse).
Impact and recommendations
Okta says the observed attacks were particularly successful against organizations running on the Okta Classic Engine with ThreatInsight configured in Audit-only mode rather than Log and Enforce mode.
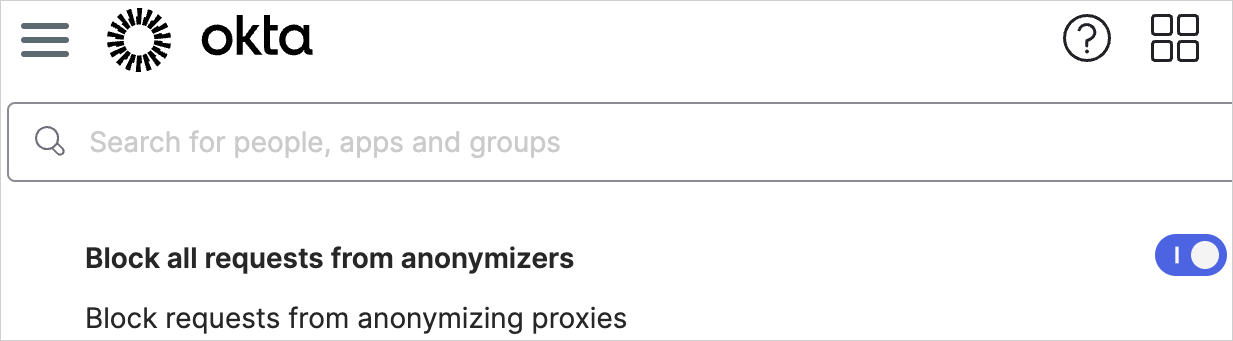
Likewise, organizations that do not deny access from anonymizing proxies also saw a higher attack success rate. The attacks were successful for a small percentage of customers Okta said.
The company provides a set of actions that can block these attacks at the edge of the network:
- enable ThreatInsight in Log and Enforce Mode to block IP addresses known for involvement in credential stuffing proactively before they can even attempt authentication.
- deny access from anonymizing proxies to proactively block requests that come through shady anonymizing services.
- switching to Okta Identity Engine, which offers more robust security features, including CAPTCHA challenges for risky sign-ins and passwordless authentication options like Okta FastPass.
- implement Dynamic Zones which enables organizations to specifically block or allow certain IPs and manage access based on geolocation and other criteria.


Comments