Over 92,000 exposed D-Link NAS devices have a backdoor account
A threat researcher has disclosed a new arbitrary command injection and hardcoded backdoor flaw in multiple end-of-life D-Link Network Attached Storage (NAS) device models..
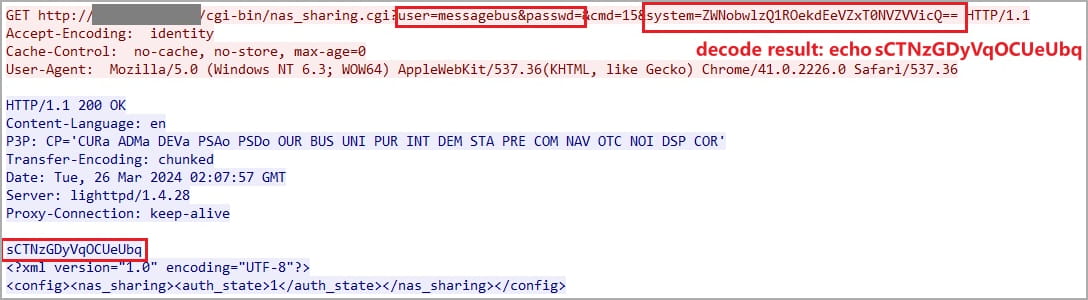
The researcher who discovered the flaw, 'Netsecfish,' explains that the issue resides within the'/cgi-bin/nas_sharing.cgi' script, impacting its HTTP GET Request Handler component.
The two main issues contributing to the flaw, tracked as CVE-2024-3273, are a backdoor facilitated through a hardcoded account (username: "messagebus" and empty password) and a command injection problem via the "system" parameter.
When chained together, any attacker can remotely execute commands on the device.
The command injection flaw arises from adding a base64-encoded command to the "system" parameter via an HTTP GET request, which is then executed.
"Successful exploitation of this vulnerability could allow an attacker to execute arbitrary commands on the system, potentially leading to unauthorized access to sensitive information, modification of system configurations, or denial of service conditions," warns the researcher.
The device models impacted by CVE-2024-3273 are:
- DNS-320L Version 1.11, Version 1.03.0904.2013, Version 1.01.0702.2013
- DNS-325 Version 1.01
- DNS-327L Version 1.09, Version 1.00.0409.2013
- DNS-340L Version 1.08
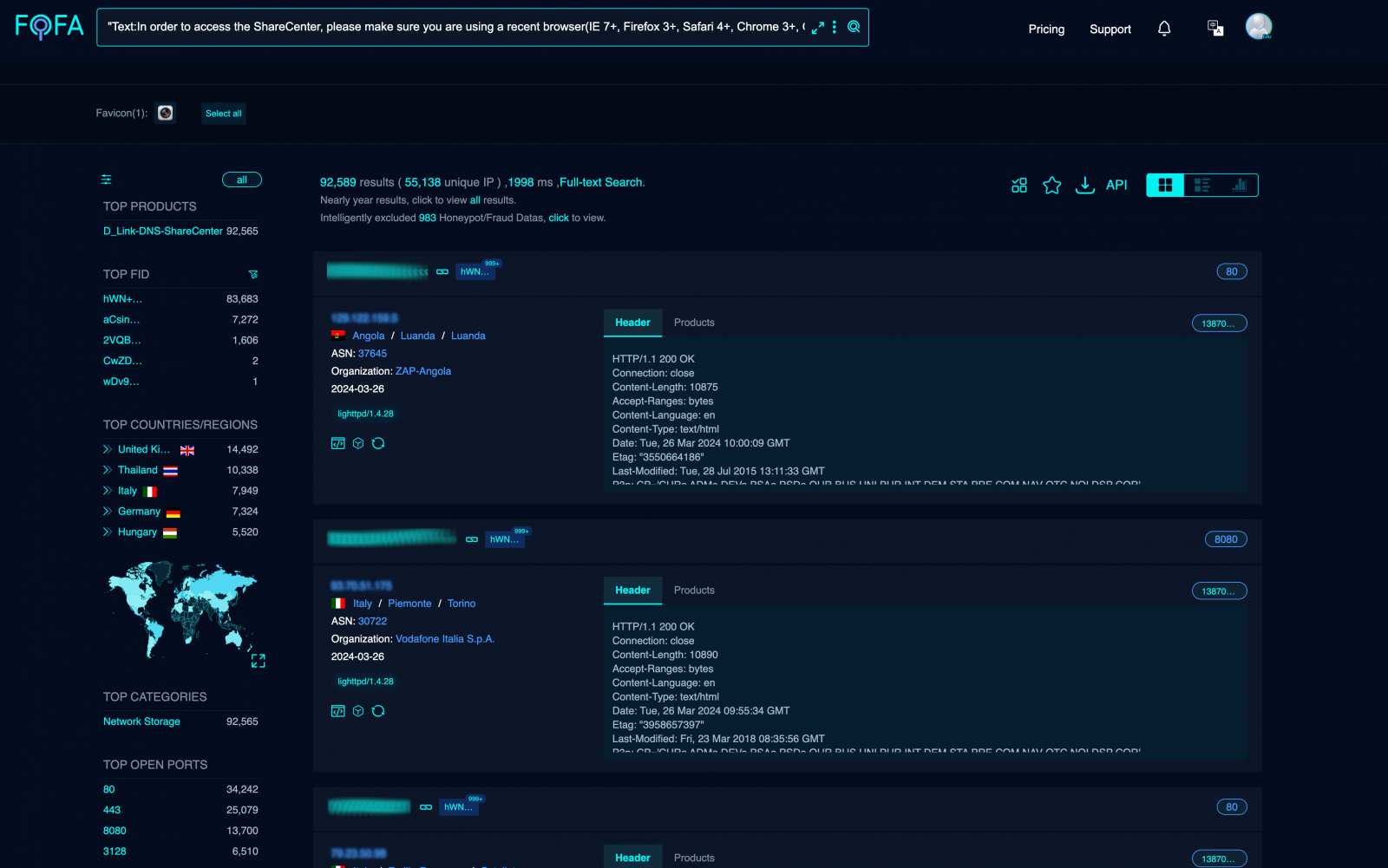
Netsecfish says network scans show over 92,000 vulnerable D-Link NAS devices exposed online and susceptible to attacks through these flaws.
No patches available
After contacting D-Link about the flaw and whether a patch would be released, the vendor told us that these NAS devices had reached the end of life (EOL) and are no longer supported.
"All D-Link Network Attached storage has been End of Life and of Service Life for many years [and] the resources associated with these products have ceased their development and are no longer supported," stated the spokesperson.
"D-Link recommends retiring these products and replacing them with products that receive firmware updates."
The spokesperson also reported that the impacted devices do not have automatic online updating capabilities or customer outreach features to deliver notifications, like current models.
Hence, the vendor was limited to a security bulletin published yesterday to raise awareness about the flaw and the need to retire or replace those devices immediately.
D-Link has set up a dedicated support page for legacy devices where owners can navigate archives to find the latest security and firmware updates.
Those who insist on using outdated hardware should at least apply the latest available updates, even if those won't address newly discovered problems like CVE-2024-3273.
Furthermore, NAS devices should never be exposed to the internet as they are commonly targeted to steal data or encrypt in ransomware attacks.


Comments