RansomHouse gang automates VMware ESXi attacks with new MrAgent tool
The RansomHouse ransomware operation has created a new tool named 'MrAgent' that automates the deployment of its data encrypter across multiple VMware ESXi hypervisors.
RansomHouse is a ransomware-as-a-service (RaaS) operation that emerged in December 2021 and is using double extortion tactics. In May 2022, the operation set up a dedicated victim extortion page on the dark web.
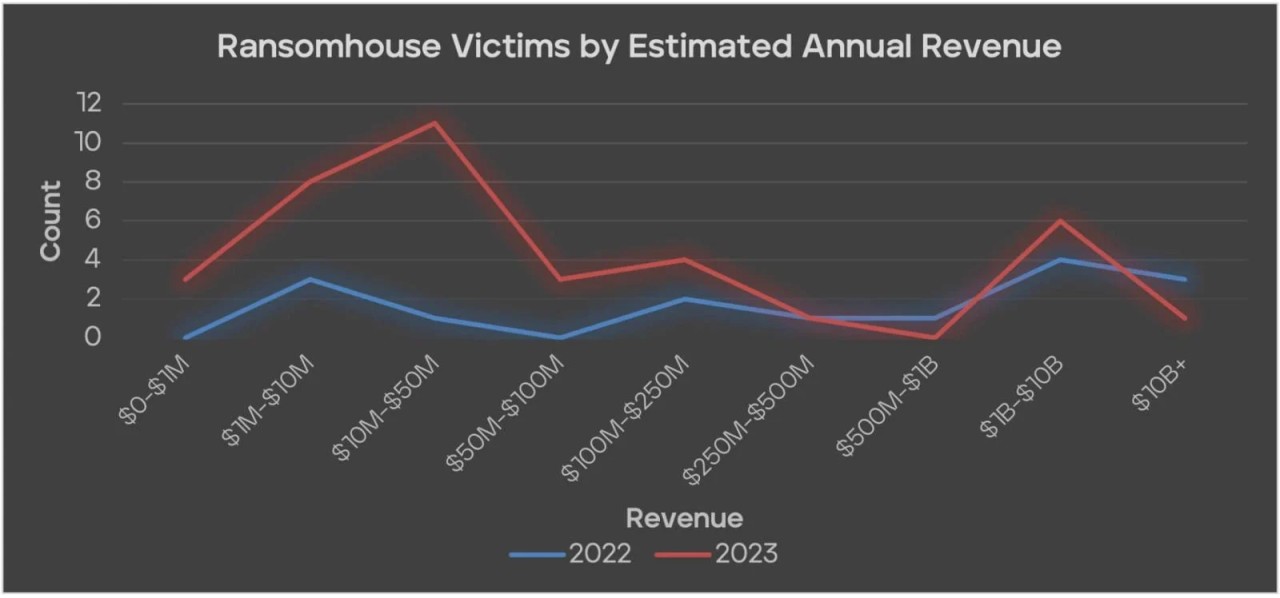
Although the RansomHouse gang was not as active as more infamous groups like LockBit, ALPHV/Blackcat, Play, or Clop, Trellix reports that it targeted large-sized organizations throughout last year.
MrAgent vs. ESXi
Ransomware groups target ESXi servers because they deploy and serve virtual computers that typically hold valuable data that can be used in the subsequent extortion process.
Also, ESXi servers often run critical applications and services for businesses, including databases and email servers, so the operational disruption from the ransomware attack is maximized.
Trellix analysts in collaboration with Northwave have spotted a new binary used in RansomHouse attacks that appears to be specifically designed for streamlining the gangs attacks on ESXi systems.
The sample was first discovered by researcher Florian Roth, while MalwareHunterTeam was the first to tweet about it in September 2023.
MrAgent's core function is to identify the host system, turn off its firewall, and then automate the ransomware deployment process across multiple hypervisors simultaneously, compromising all managed VMs.
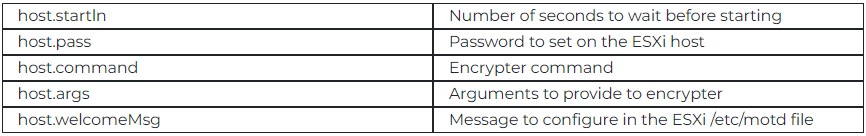
The tool supports custom configurations for ransomware deployment received directly from the command and control (C2) server.
These configurations include setting passwords on the hypervisor, configuring the encrypter command and its arguments, scheduling an encryption event, and changing the welcome message displayed on the hypervisor's monitor (to display a ransom notice).
MrAgent can also execute local commands on the hypervisor received from the C2 again to delete files, drop active SSH sessions to prevent interference during the encryption process and send back information about the running VMs.
By disabling the firewall and potentially dropping non-root SSH sessions, MrAgent minimizes the chances of detection and intervention by administrators while simultaneously increasing the impact of the attack by targeting all reachable VMs at once.
Trellix says it has spotted a Windows version of MrAgent, which retains the same core functionality but features OS-specific adaptations such as using PowerShell for certain tasks.
Using the MrAgent tool across different platforms shows RansomHouse's intention to extend the tool's applicability and maximize the impact of their campaigns when the target uses both Windows and Linux systems.
"The efforts to (further) automate the steps that are otherwise often executed manually shows both the interest and willingness of the attacking affiliate to target large networks," Trellix says in the report.
The security implications of tools like MrAgent are severe, so defenders must implement comprehensive and robust security measures, including regular software updates, strong access controls, network monitoring, and logging to defend against such threats.


Comments