Toronto Public Library confirms data stolen in ransomware attack
The Toronto Public Library (TPL) confirmed that the personal information of employees, customers, volunteers, and donors was stolen from a compromised file server during an October ransomware attack.
According to TPL, the attackers stole "a large number of files from a file server" containing data of Toronto Public Library (TPL) and the Toronto Public Library Foundation (TPLF) employees, going back to 1998.
"Information related to these individuals was likely taken, including their name, social insurance number, date of birth and home address. Copies of government-issued identification documents provided to TPL by staff were also likely taken," the library said in an update to its incident report.
"Our cardholder and donor databases are not affected. However, some customer, volunteer and donor data that resided on the compromised file server may have been exposed."
The library has yet to disclose what customer data was stolen and how many customers were affected by the data breach.
TPL says it hasn't paid a ransom after the attack, and it's working with external cybersecurity experts to investigate the incident. It also reported the breach to Ontario's Information and Privacy Commissioner and filed a report with the Toronto Police.
As Canada's largest public library system, TPL operates on a budget exceeding $200 million, has a membership base of 1,200,000 registered individuals, and provides access to 12 million books across 100 branch libraries throughout the city.
Black Basta ransomware attack
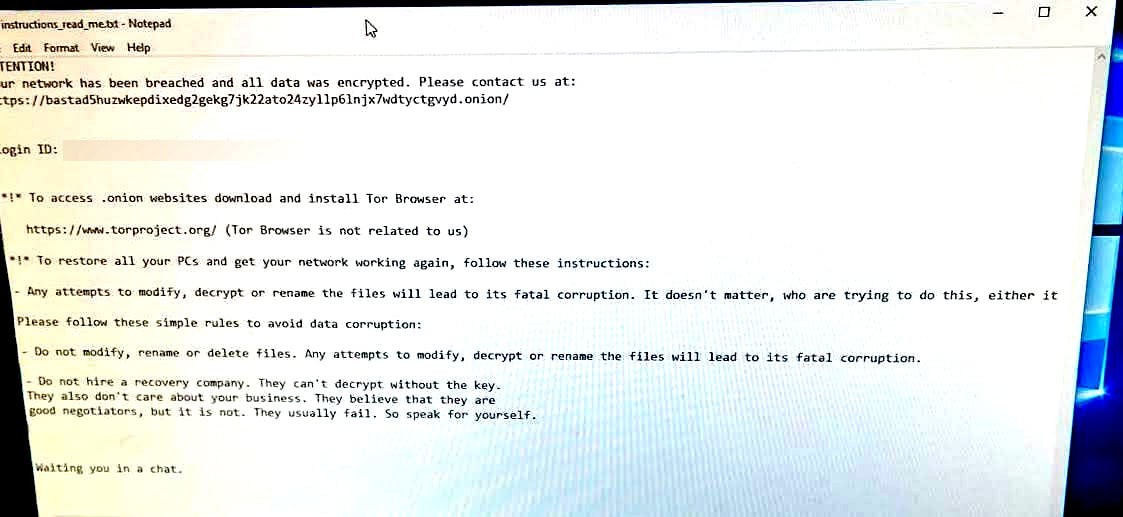
While the library hasn't yet attributed the attack to a specific ransomware operation, it has been learned that the Black Basta ransomware gang was behind the October 28 attack after seeing a photo of a ransom note shown on a TPL workstation.
As a TPL employee indicated, the attack occurred overnight on October 27, disrupting numerous services by Saturday morning.
We were also told that the attack had minimal impact on TPL's email services and didn't affect the library's phone system. While employees logged into their Office 365 accounts could still access their emails, those who were logged out couldn't access their email accounts.
The organization's primary servers (housing sensitive data) were also not encrypted, hinting at the possibility that the Black Basta operators didn't have full access to the library's networks and data.
As a precautionary measure to prevent the spread of the malware, TPL shut down all other internal systems after the attack was detected.
Black Basta emerged as a Ransomware-as-a-Service (RaaS) operation in April 2022, with double-extortion attacks targeting many corporate entities.
After the Conti ransomware gang stopped operating in June 2022 following a sequence of humiliating data breaches, the cybercrime syndicate fragmented into smaller factions, one of which is presumed to be Black Basta.
"The threat group's prolific targeting of at least 20 victims in its first two weeks of operation indicates that it is experienced in ransomware and has a steady source of initial access," the Department of Health and Human Services security team said in March.
"The level of sophistication by its proficient ransomware operators, and reluctance to recruit or advertise on Dark Web forums, supports why many suspect the nascent Black Basta may even be a rebrand of the Russian-speaking RaaS threat group Conti, or also linked to other Russian-speaking cyber threat groups."
Moreover, Black Basta has been linked with the FIN7 hacking group, a well-known financially motivated cybercrime group.
Since it surfaced, the Russian-speaking ransomware gang has breached and extorted a wide range of high-profile victims, including the American Dental Association, Sobeys, Knauf, Yellow Pages Canada, UK outsourcing company Capita, the Rheinmetall German defense contractor, and most recently, U.S. government contractor ABB.


Comments