WordPress AIOS plugin used by 1M sites logged plaintext passwords
The All-In-One Security (AIOS) WordPress security plugin, used by over a million WordPress sites, was found to be logging plaintext passwords from user login attempts to the site's database, putting account security at risk.
AIOS is an all-in-one solution developed by Updraft, offering web application firewall, content protection, and login security tools for WordPress sites, promising to stop bots and prevent brute force attacks.
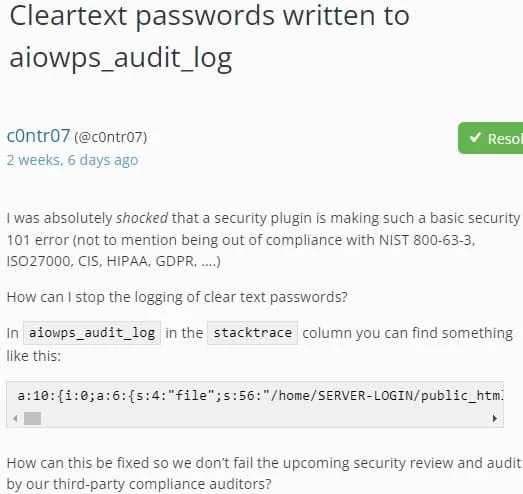
Roughly three weeks ago, a user reported that the AIOS v5.1.9 plugin was not only recording user login attempts to the aiowps_audit_log database table, used to track logins, logouts, and failed login events but also recording the inputted password.
The user expressed concern that this activity violates multiple security compliance standards, including NIST 800-63 3, ISO 27000, and GDPR.
However, Updraft's support agent responded by saying it was a "known bug" and delivering a vague promise about a fix being available in the next release.
After realizing the criticality of the problem, the support offered development builds of the upcoming release to concerned users two weeks ago. Still, those attempting to install the development builds reported website problems and that the password logs weren't removed.
Fix now available
Eventually, on July 11, the AIOS vendor released version 5.2.0, which includes a fix to prevent saving plaintext passwords and clears out old entries.
"AIOS release 5.2.0 and newer updates have fixed a bug in 5.1.9 which resulted in users' passwords being added to the WordPress database in plain text," reads the release announcement.
"This would be a problem if [malicious] site administrators were to try out those passwords on other services where your users might have used the same password."
If the exposed people's login details are not protected by two-factor authentication on these other platforms, rogue admins could easily take over their accounts.
Apart from the malicious admin scenario, websites using AIOS would face elevated risk from hacker breaches, as a bad actor gaining access to the site's database could exfiltrate user passwords in plaintext form.
It has more than 1 million active installations btw. So far the developer haven’t even told the users to change all passwords. Due to the scale, we will 100% see hackers harvest the credentials from the logs of compromised sites that run (or has run) this plugin.
— Oliver Sild (@OliverSild) July 12, 2023
At the time of writing, WordPress.org stats show that roughly one-fourth of AIOS users have applied the update to 5.2.0, so more than 750,000 sites remain vulnerable.
Unfortunately, with WordPress a common target for threat actors, there is a chance that some of the sites using AIOS were compromised already, and considering that the issue has been circulated online for three weeks now, hackers have had plenty of opportunity to take advantage of the plugin's creator's slow response.
Also, it is unfortunate that at no point during the exposure period did Updraft warn its users about the elevated risk of exposure, advising them on what actions to take.
Websites using AIOS should now update to the latest version and ask users to reset their passwords.


Comments