CPRA (California Privacy Rights Act) Compliance Guide
The CPRA comes into effect on January 1, 2023 but government enforcement action won't take place until July 1, 2023.
Ideally, your organization should have achieved compliance by January 1, 2022, since the CPRA's look-back provision covers all information collected on or after January 1, 2022.
Whether you're assessing CPRA compliance gaps in your current compliance strategy or creating a framework for a compliance plan, this article will help.
Who Must Comply with CPRA?
The CPRA applies to all for-profit organizations that have generated $25 million in revenue globally or in the previous calendar year with at least one employee in California.
What's the Difference Between the CCPA and the CPRA?
The CPRA increases the violation conditions of the CCPA by broadening consumer rights and strengthening the enforcement of provisions of the CCPA. In other words, it's much easier to break the rules of the CPRA than the CCPA.

The primary differences between the two regulations are summarized below:
New Sensitive Personal Information Category
The CPRA introduces a new category of sensitive data -Sensitive Personal Information (SPI). This new category expands the CCPA's definition of "personal information" to include all of the following:
- Social Security Number;
- Driver's license;
- State identification card;
- Passport Number;
- Financial account information and log-in credentials;
- Debit Card or Credit Card number along with access codes;
- Precise geolocation data;
- Religious or philosophical beliefs;
- Ethnic origin;
- Contents of communication;
- Genetic data;
- Biometric data;
- Health information;
- Information about sex or sexual orientation
Broadened Provisions
CCPA provisions that have been broadened in the CPRA are as follows:
- The rights of California residents to request that their personal information is deleted and to opt-out of the sale of their personal information are expanded.
- Businesses must provide additional transparency about how they collect and use personal information, including specific information about the categories of personal information they collect and the purposes for which they use it.
- Consumers have the right to opt-out of data sharing for cross-context behavioral advertising.
- Businesses must give consumers access to their data retention policies.
- Businesses shouldn't store personal data longer than reasonably necessary.
- Under the CPRA privacy legislation, consumers have a right to request the deletion of their collected personal data across all third-party beneficiaries. A business must action each request with all third-party vendors service providers, and contractors.
- Consumers have a right to request a business to disclose the data categories and specific pieces of collected personal information linked to them.
- Consumers have a right to data portability - requesting certain elements of collected personal information to be transferred to another entity.
Strengthened Provisions
CCPA provisions that have been strengthened in the CPRA are as follows:
- The CPRA establishes a new California Privacy Protection Agency, which will have stronger enforcement powers and be responsible for issuing regulations to implement the law.
- The CPRA includes stricter requirements for contracts between businesses and service providers and requires service providers to implement stronger security measures to protect personal information.
- The "cure period" - a grace timeframe for correcting a violation - is no longer a set period (30 days for the CCPA). Instead, the California Privacy Protection Agency decides on an appropriate "cure period" based on the nature of the violation and any other relevant factors.
- Penalties for mishandling children's personal information have tripled to $7,500 (compared to $2,500 under the CCPA).
- The CPRA expands its definition of a data breach to include email account leaks - especially if they lead to the disclosure of personal information linked to Californian residents, and security question leaks - account security questions that help users recover forgotten passwords.
Broadened Notification Provisions
The following notification provisions have been expanded in the CPRA:
- All data subjects (including consumers, job applicants, employees and other workers) must be notified of an intention to collect their personal data at the point of data collection (not after the fact). Such disclosures must also include retention periods for all collected data.
- While the CCPA is very vague about its disclosure period following a data breach, the CPRA is more specific. Under the CPRA, compromised businesses must disclose data breaches to the California Privacy Protection Agency and any affected California residents within 15 days of becoming aware of an incident.
Other CPRA Requirements
Other regulatory requirements under CPRA include:
- Cybersecurity Audits - Any organization storing data that could "present a significant risk to its consumer' if compromised must perform independent annual cybersecurity audits and submit them to the CCPA.
- Risk Assessments - Organizations must perform regular risk assessments of processes involving sensitive customer data to determine their resilience to compromise.
The following provisions mirror the sensitive data safeguards of the GDPR.
- Data Minimization - Organizations must limit the amount of personal data collected to the minimum amount necessary for its intended purpose. All intended uses for collected data must be disclosed to Californian users before collection.
- Purpose Limitation - Collected personal information must only be processed in line with disclosed purposes if any processing requirements change.
- Storage Limitation - Collected personal information must not be retained for longer than "reasonably necessary." All retention periods must be clearly disclosed to consumers at the point of collection.
New CPRA Regulation Requirements
The following provisions are new CPRA requirements that differ from the CCPA:
- California residents have a right to ask organizations to limit the use of their Sensitive Personal Information (SPI).
- Consumers have a right to request amendments to any incorrect consumer data records.
- Consumers have the right to know the details about automated decision-making processes based on their collected personal data. Organizations must honor all such consumer requests.
- Consumers have the right to opt out of automated decision-making technology.
- Businesses must provide minors with opt-in consent for collecting their personal information. If a minor under 16 denies such a request, the business must wait at least 12 months or until the minor turns 16 to ask for opt-in consent again.
- Businesses must clearly disclose intentions to sell or share personal information linked to minors.
6-Stage Framework for CPRA Compliance
Compliance with the data privacy standards of the CPRA can be achieved with the following framework:
1. Implement a Risk Assessment Solution
To meet CPRA's requirements for regular risk assessments of processes involving sensitive customer data, an ideal risk assessment solution should be capable of creating custom questionnaires to address unique data processing queries.
Because the CPRA was born from the CCPA, CCPA compliance establishes a compliance foundation for the CPRA. If you still need to implement a CPRA compliance program, you could scope the required effort by performing a high-level gap analysis against the security standards of the CCPA.
2. Identify All Processes and Assets Storing Personal Information
To determine the degree of security controls required to meet CPRA's data security standards, you need to identify the types of personal information your business collects and the different processes and assets that utilize them.
With a complex digital ecosystem, this effort can be challenging, but it is possible with digital footprint mapping.
Your digital footmaping efforts should extend to the third-party vendor network to identify all third-party vendors with access to personal data. This will allow you to adjust your third-party risk assessment efforts to prioritize vendors with the highest degree of sensitive data access and, therefore, the highest potential of suffering compromise - an effort supporting the CPRA's requirement of focusing on entities representing a "significant risk to consumers" if compromised.
The process of prioritizing high-risk vendors is known as "Vendor Tiering."
3. Review and Update Third-Party Contracts
Update all third-party vendor contracts to include a stipulation to action all consumer personal data deletion requests promptly. Also, update contracts to include stricter data security requirements for all third-party vendors with access to personal data.
4. Design Internal Procedures for Actioning Data Deletion Requests
To prevent personal data deletion requests from being overlooked, design internal processes for actioning all requests and monitoring their completion. Having a documented data deletion process in place will help you fulfill requests from California residents to delete their personal information quickly, ensuring compliance with the data deletion provisions of the CPRA.
5. Deploy Security Controls Across the Cyber Attack Pathway
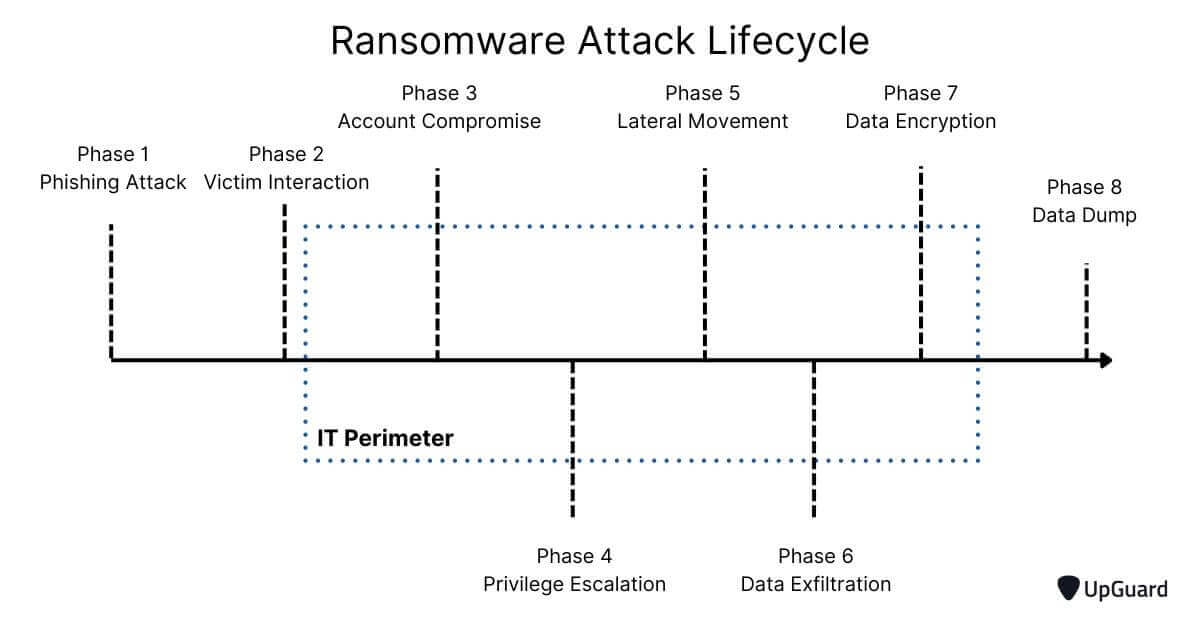
To minimize the chances of suffering a data breach, security controls should be developed across each stage of the cyber attack pathway - a sequence of cyberattack events common to most data breach attempts.
For best results, your security control strategy should be based on one of the most styles of cyberattacks - ransomware attacks.
6. Monitor Security Postures of all Third-Party Vendors
The CPRA expects all third parties (including service providers and contractors) with sensitive data access to have sufficient security measures in place to withstand data breach attempts.
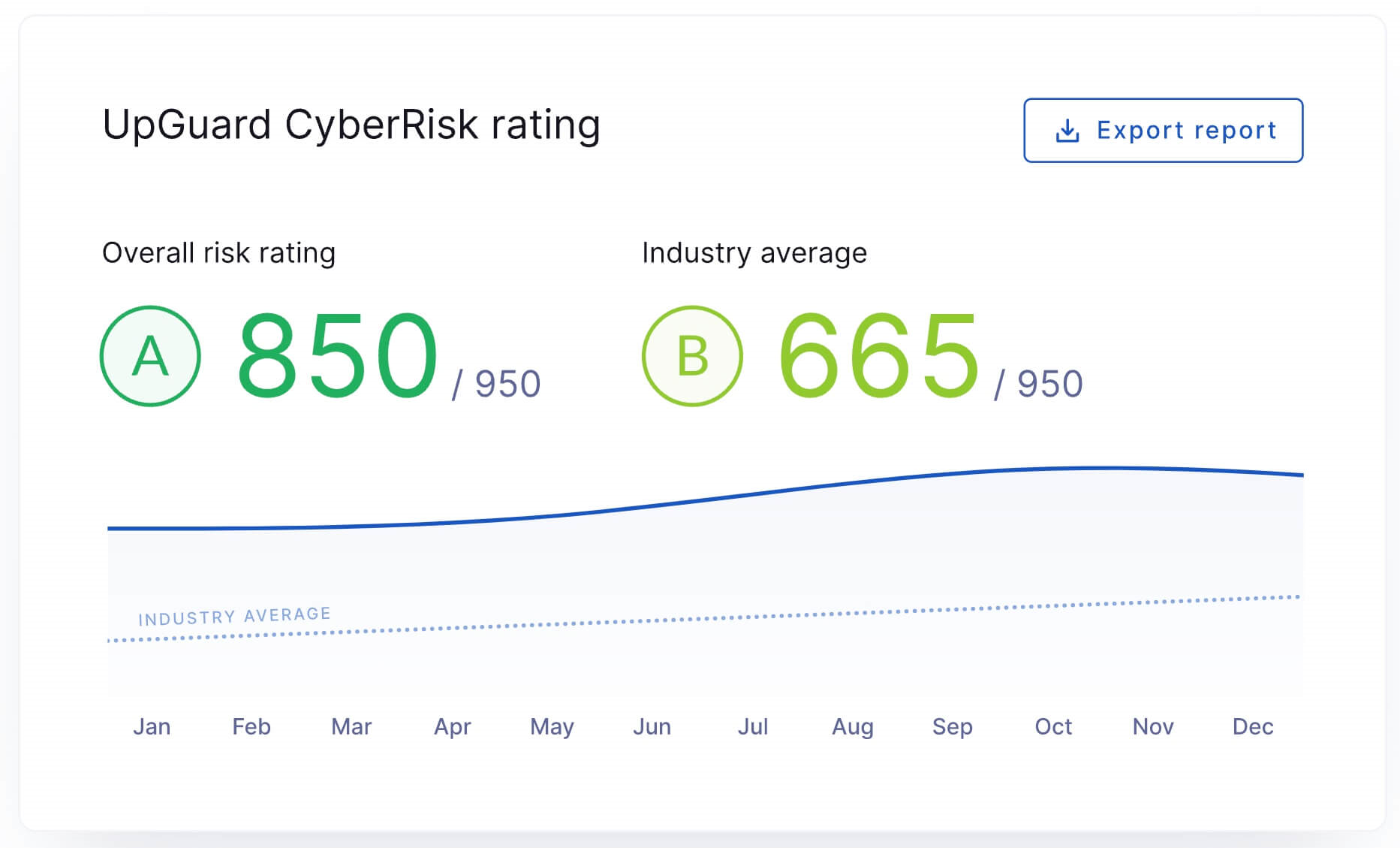
Each third-party vendor's risk of suffering a data breach can be measured with security ratings - a quantitative measurement of an organization's security posture. With a security ratings solution, you can easily monitor the cybersecurity postures of all your third-party vendors from a single-pane-of-glass view and track deviations in real-time.

Comments