Dell Compellent hardcoded key exposes VMware vCenter admin creds
An unfixed hardcoded encryption key flaw in Dell's Compellent Integration Tools for VMware (CITV) allows attackers to decrypt stored vCenter admin credentials and retrieve the cleartext password.
The flaw, tracked as CVE-2023-39250, is caused by a static AES encryption key, shared across all installs, that is used to encrypt the vCenter credentials stored in the program's configuration file.
Dell Compellent is a line of enterprise storage systems offering features such as data progression, live volume, thin provisioning, data snapshots and cloning, and integrated management.
The software supports storage integration with VMware vCenter, a widely used platform for managing ESXi virtual machines.
However, to integrate the client, it must be configured with VMware vCenter credentials, which are stored in the Dell program's encrypted configuration file.
A hardcoded AES encryption key
LMG Security's researcher Tom Pohl, discovered in a penetration exercise that Dell CITV contains a static AES encryption key that is identical for all Dell customers across all installs.
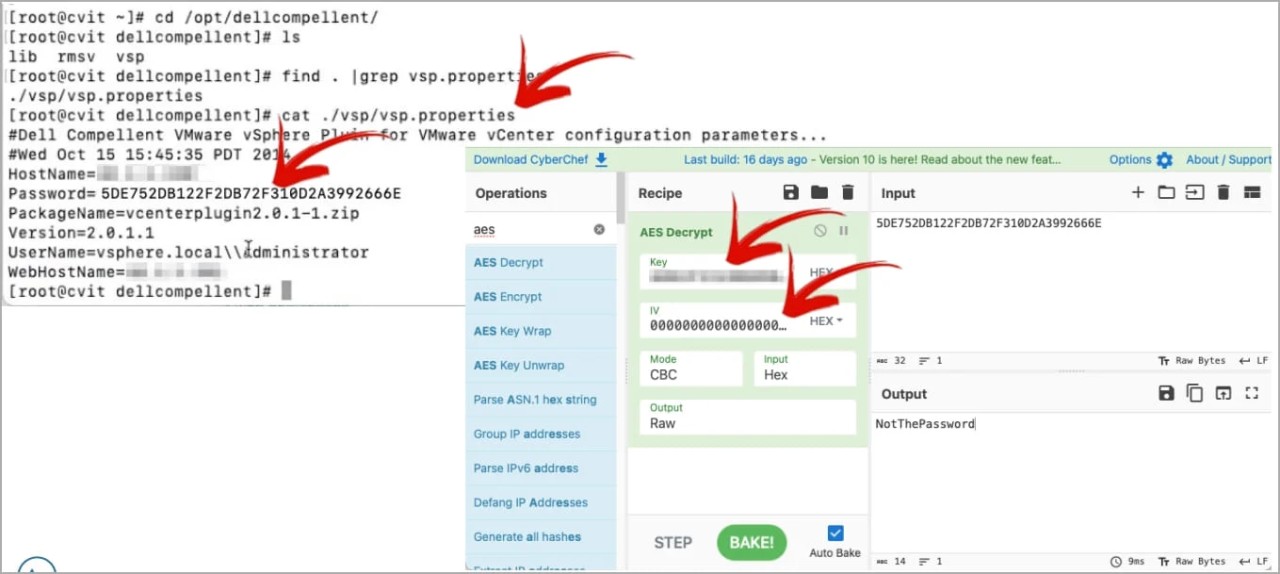
This AES encryption key is used to encrypt the CITV configuration file containing the program's settings, including the entered vCenter admin credentials.
As AES is a symmetric cipher, it uses the same key for encrypting and decrypting data. This allows an attacker who extracts the key to easily decrypt the configuration file and retrieve the encrypted password.
"The Dell software needs administrative vCenter credentials to function correctly, and it protects those credentials in their config files with a static AES key," Pohl told BleepingComputer.
"Dell is interacting with vCenter servers and is keeping its credentials in an encrypted config file that should be completely inaccessible for viewing by anything or anyone other than the Dell software."
"Attackers should not be able to get access to the contents of that file, but it is accessible. However, due to this newly discovered vulnerability, attackers can extract the encryption key that the Dell software is using to protect the contents of that file."
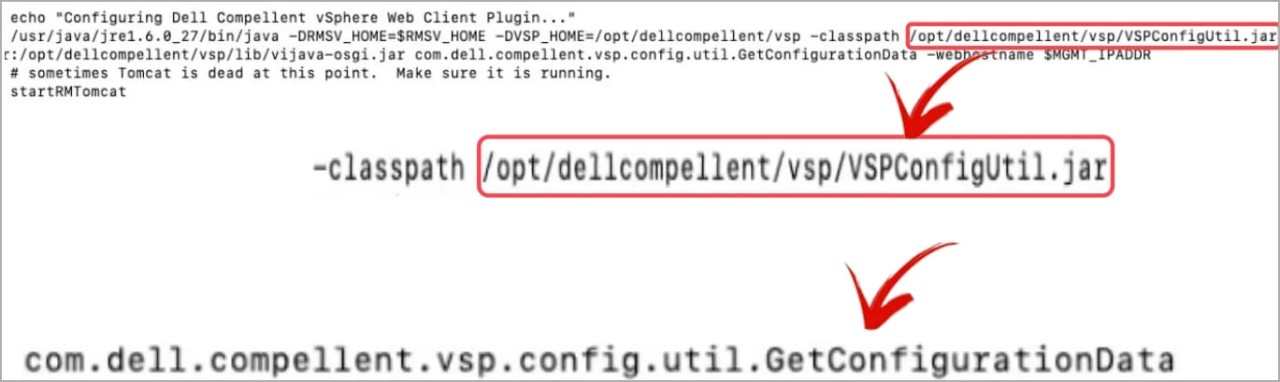
LMG Security's team found that the Dell Compellent software directory contains a JAR file that, when decompiled, revealed a hardcoded static AES key.
Using this AES key, Pohl could decrypt the Dell Compellent configuration file and retrieve the user name and password for the VMware vCenter administrator, as shown below.
The server containing that key was accessible using weak credentials (admin/admin). However, as seen repeatedly, threat actors can gain access to servers in various ways due to vulnerabilities or bad practices.
Also, the issue could be exploitable by rogue insiders or low-privileged external attackers who have access to Dell CITV.
In this instance, the LMG team could have gone further by leveraging access to domain controls but instead opted to create a domain admin account, exploiting the opportunity when a network admin mistakenly left their console unlocked.
The analysts emailed Dell to inform them about their discovery on April 11th, 2023, but the computer and software vendor initially dismissed the report, misunderstanding the scope.
After further communication, Dell promised to roll out a fix by November 2023.
As the standard 90-day vulnerability disclosure policy has expired, Pohl has publicly shared his research in a DEFCON session titled "Private Keys in Public Places."
Pohl discovered similar hardcoded keys in Netgear and Fortinet in 2020, which were subsequently fixed.
Update 8/10/23: After the publishing of this story, Dell shared an advisory for CVE-2023-39250 that suggests users change the root password of their Compellent devices as a mitigation.
"Dell Technologies released instructions for a full workaround to address a vulnerability in the Dell Storage Compellent Integration Tools for VMware product. Customers should review Dell Security Advisory DSA-2023-282 at their earliest convenience for details. The security of our products is a top priority and critical to protecting our customers."
by Dell Technologies
However, it is unclear how this would prevent a local user from extracting the AES key.
Follow up questions have been sent regarding this advisory and will update this article if we receive a response.


Comments