CISA: New Whirlpool backdoor used in Barracuda ESG hacks
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has discovered that the backdoor malware named 'Whirlpool' used in attacks on compromised Barracuda Email Security Gateway (ESG) devices.
In May, Barracuda revealed a suspected pro-China hacker group (UNC4841) had breached ESG (Email Security Gateway) appliances in data-theft attacks using the CVE-2023-2868 zero-day vulnerability.
CVE-2023-2868 is a critical severity (CVSS v3: 9.8) remote command injection vulnerability impacting Barracuda ESG versions 5.1.3.001 through 9.2.0.006.
It was later discovered that the attacks started in October 2022 and were used to install previously unknown malware named Saltwater and SeaSpy and a malicious tool called SeaSide to establish reverse shells for easy remote access.
Instead of fixing devices with software updates, Barracuda offered replacement devices to all affected customers at no charge, indicating that the attacks were more damaging than originally thought.
CISA has since shared further details about an additional malware named Submariner that was deployed in the attacks.
Whirlpool malware
Yesterday, CISA disclosed the discovery of another backdoor malware named 'Whirlpool' [VirusTotal] that was found to be used in the attacks on Barracuda ESG devices.
The discovery of Whirlpool makes this the third distinct backdoor used in the attacks targeting Barracuda ESG, once again illustrating why the company chose to replace devices rather than fix them with software.
"This artifact is a 32-bit ELF file that has been identified as a malware variant named "WHIRLPOOL," reads CISA's updated Barracuda ESG malware report.
"The malware takes two arguments (C2 IP and port number) from a module to establish a Transport Layer Security (TLS) reverse shell."
"The module that passes the arguments was not available for analysis."
From submissions to VirusTotal, the Whirlpool malware appears to have run under the 'pd' process.
Mandiant was the first to document Whirlpool in a June 2023 report, attributing its use to Chinese threat actors.
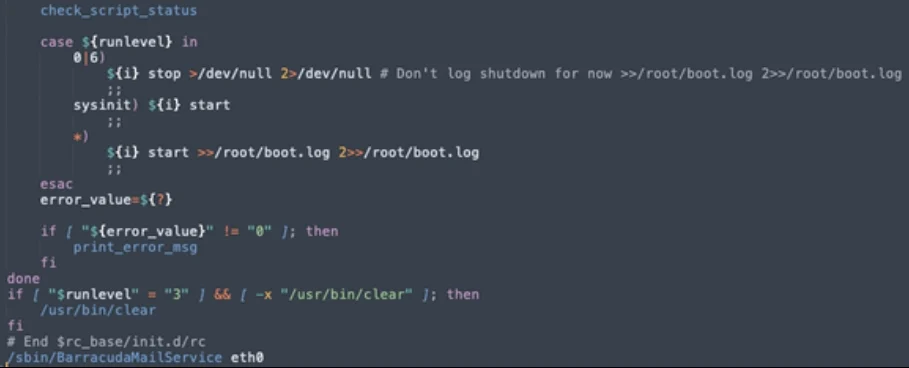
Previously, on May 30, 2023, Barracuda found SeaSpy on hacked ESG appliances, a persistent passive backdoor that masquerades as a legitimate service, namely "BarracudaMailService," and runs commands on behalf of the threat actors.
On July 28, 2023, CISA warned of a previously unknown backdoor in breached Barracuda devices named 'Submarine.'
Submarine resides in the SQL database of ESG, allowing root access, persistence, and command and control communications.
Indicators of compromise and YARA rules that help detect infections by the four newly discovered variants of SeaSpy and Whirlpool are provided in a separate document.
If you identify suspicious activity on your Barracuda ESG appliance or discover signs of compromise by any of the three mentioned backdoors, you are urged to contact CISA's 24/7 Operations Center at "


Comments