Evasive Sign1 malware campaign infects 39,000 WordPress sites
A previously unknown malware campaign called Sign1 has infected over 39,000 websites over the past six months, causing visitors to see unwanted redirects and popup ads.
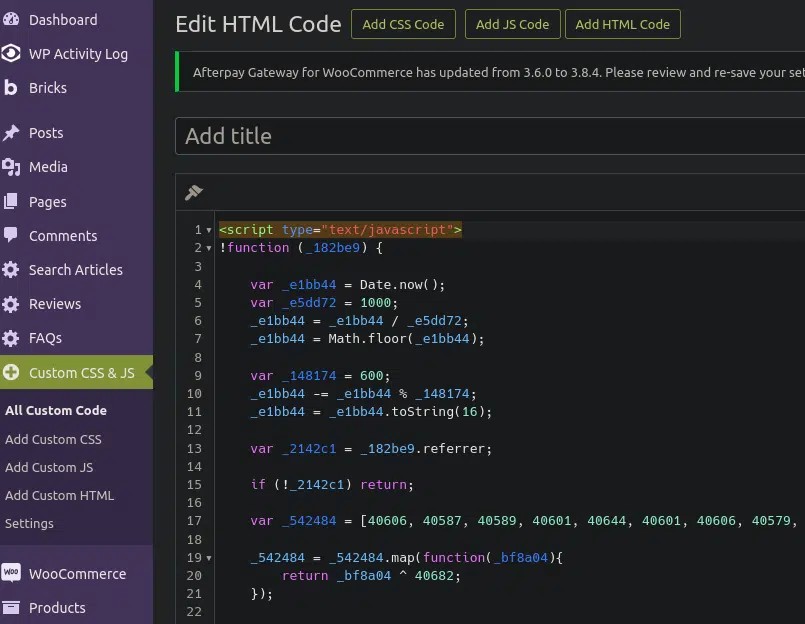
The threat actors inject the malware into custom HTML widgets and legitimate plugins on WordPress sites to inject the malicious Sign1 scripts rather than modifying the actual WordPress files.
Website security firm Sucuri discovered the campaign after a client's website randomly displayed popup ads to visitors.
The Sign1 malware campaign
While Sucuri's client was breached through a brute force attack, Sucuri has not shared how the other detected sites were compromised.
However, based on previous WordPress attacks, it probably involves a combination of brute force attacks and exploiting plugin vulnerabilities to gain access to the site.
Once the threat actors gain access, they use WordPress custom HTML widgets or, more commonly, install the legitimate Simple Custom CSS and JS plugin to inject the malicious JavaScript code.
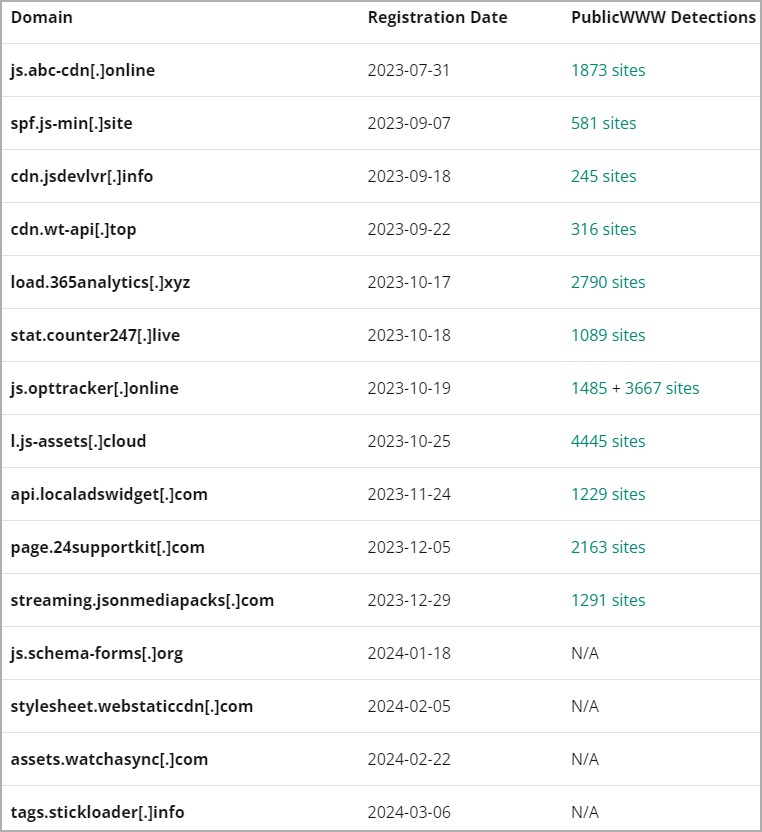
Sucuri's analysis of Sign1 shows that the malware uses time-based randomization to generate dynamic URLs that change every 10 minutes to evade blocks. The domains are registered shortly before they are used in attacks, so they're not in any blocklists.
These URLs are used to fetch further malicious scripts that are run in a visitor's browser.
Initially, the domains were hosted on Namecheap, but the attackers have now moved to HETZNER for hosting and Cloudflare for IP address obfuscation.
The injected code features XOR encoding and seemingly random variable names, making detecting it harder for security tools.
The malicious code checks for specific referrers and cookies before executing, targeting visitors from major sites like Google, Facebook, Yahoo, and Instagram and remaining dormant in other cases.
Also, the code creates a cookie on the target's browser so that the popup is displayed only once per visitor, making it less likely to generate reports towards the compromised website owner.
The script then redirects the visitor to scam sites, such as fake captchas, that try to trick you into enabling browser notifications. These notifications deliver unwanted advertisements directly to your operating system desktop.
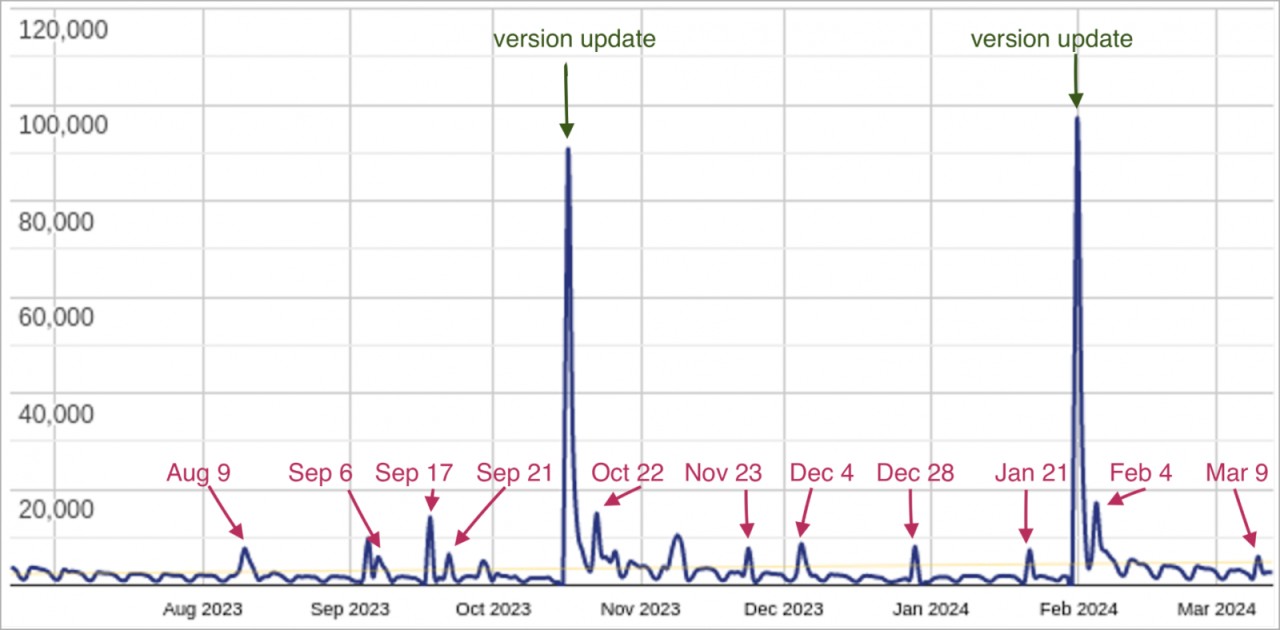
Sucuri warns that Sign1 has evolved over the past six months, with infections spiking when a new version of the malware is released.
In the past six months, Sucuri's scanners detected the malware on over 39,000 websites, while the latest attack wave, which has been underway since January 2024, has claimed 2,500 sites.
The campaign has evolved over time to become stealthier and more resilient to blocks, which is a worrying development.
To protect your sites against these campaigns, use a strong/long administrator password and update your plugins to the latest version. Also, unnecessary add-ons should be removed, which can act as a potential attack surface.


Comments