SpyAgent Android malware steals your crypto recovery phrases from images
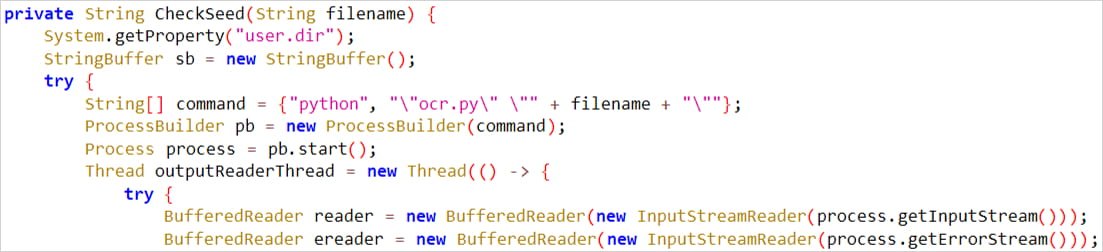
A new Android malware named SpyAgent uses optical character recognition (OCR) technology to steal cryptocurrency wallet recovery phrases from screenshots stored on the mobile device.
A cryptocurrency recovery phrase, or seed phrase, is a series of 12-24 words that acts as a backup key for a cryptocurrency wallet. These phrases are used to restore access to your cryptocurrency wallet and all of its funds in the event you lose a device, data is corrupted, or you wish to transfer your wallet to a new device.
These secret phrases are highly sought after by threat actors, as if they can gain access to it, they can use it to restore your wallet on their own devices and steal all of the funds stored within it.
As recovery phrases are 12-24 words, they are hard to remember, so cryptocurrency wallets tell people to save or print the words and store them in a safe place. To make it easier, some people take a screenshot of the recovery phrase and save it as an image of their mobile device.
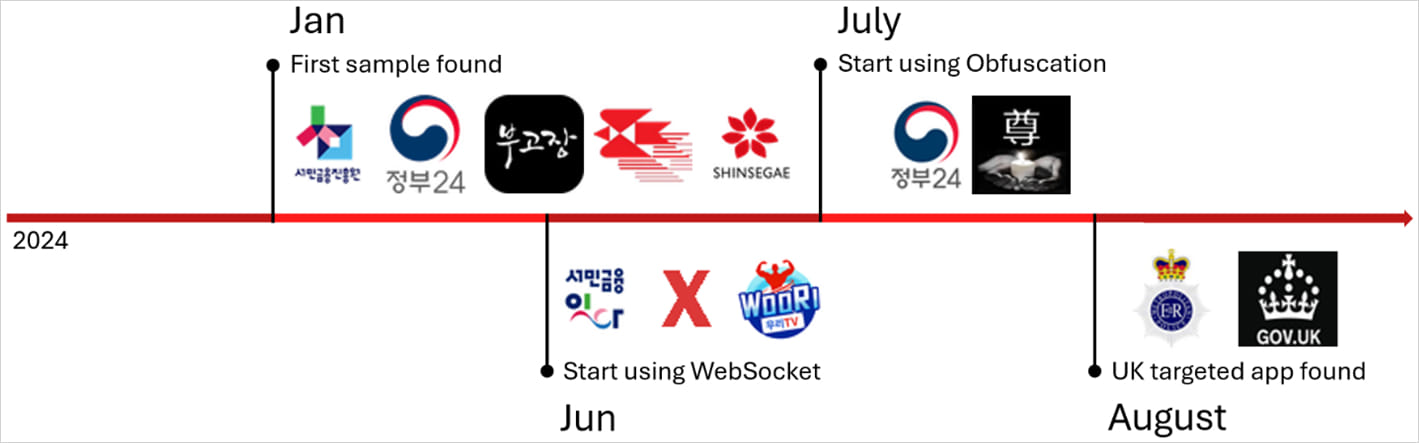
A malware operation discovered by McAfee was traced back to at least 280 APKs distributed outside of Google Play using SMS or malicious social media posts. This malware can use OCR to recover cryptocurrency recovery phrases from images stored on an Android device, making it a significant threat.
Some of the Android applications pretend to be for South Korean and UK government services, dating sites, and pornography sites.
Though the activity mainly targeted South Korea, McAfee has observed a tentative expansion to the UK and signs that an iOS variant might be in early development.
In July 2023, Trend Micro revealed two Android malware families named CherryBlos and FakeTrade, spread via Google Play, that also used OCR to steal cryptocurrency data from extracted images, so this tactic appears to be gaining traction.
SpyAgent data extraction
Once it infects a new device, SpyAgent begins sending the following sensitive information to its command and control (C2) server:
- Victim's contact list, likely for distributing the malware via SMS originating from trusted contacts.
- Incoming SMS messages, including those containing one-time passwords (OTPs).
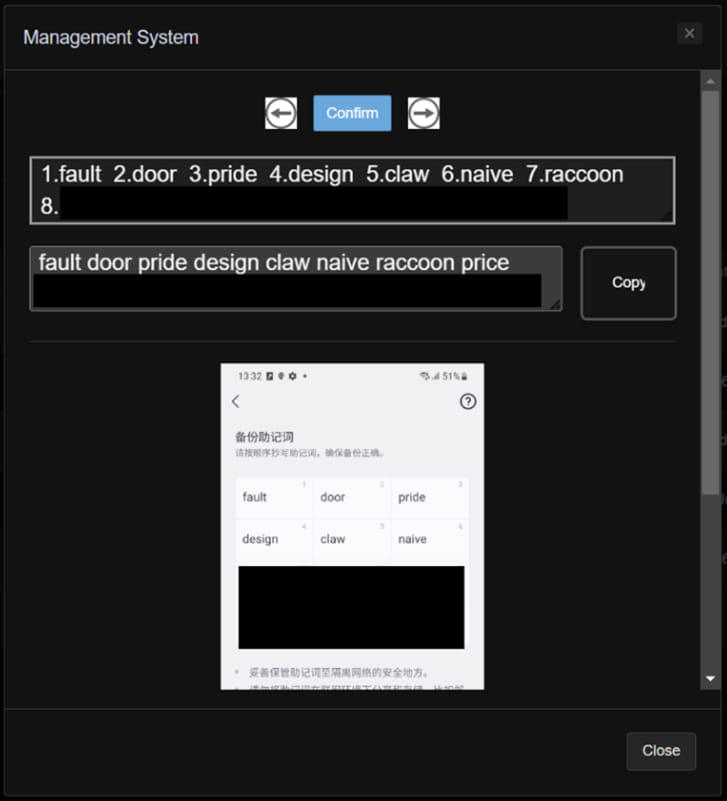
- Images stored on the device to use for OCR scanning.
- Generic device information, likely for optimizing the attacks.
SpyAgent can also receive commands from the C2 to change the sound settings or send SMS messages, likely used to send phishing texts to distribute the malware.
Exposed infrastructure
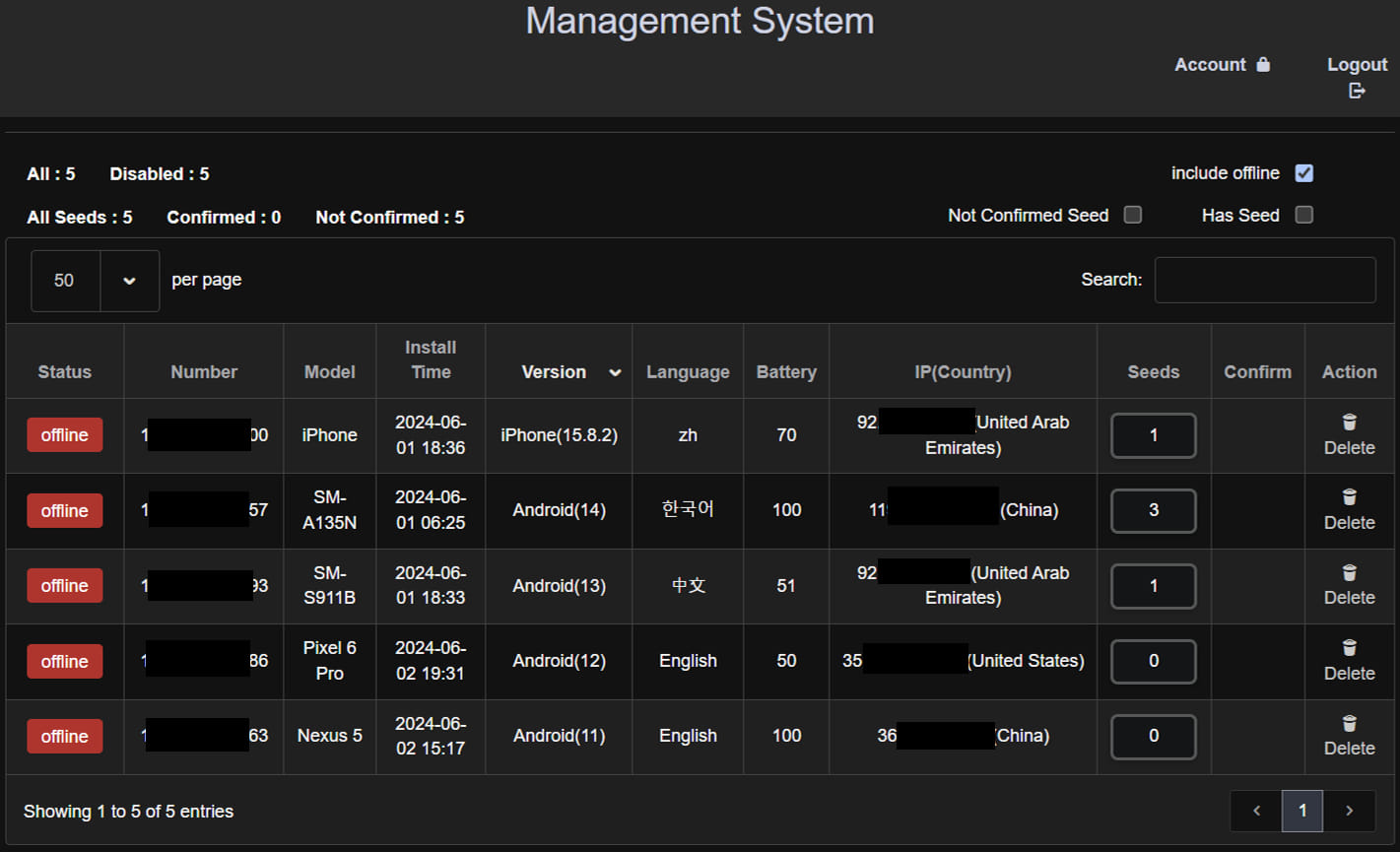
McAfee found that the operators of the SpyAgent campaign did not follow proper security practices in configuring their servers, allowing the researchers to gain access to them.
Admin panel pages, as well as files and data stolen from victims, were easily accessible, allowing McAfee to confirm that the malware had claimed multiple victims.
The stolen images are processed and OCR-scanned on the server side and then organized on the admin panel accordingly to allow easy management and immediate utilization in wallet hijack attacks.
To mitigate this risk on Android, it is important not to install Android apps outside of Google Play, as they are commonly used to distribute malware.
Furthermore, users should disregard SMS messages pointing to APK download URLs and revoke dangerous permissions that seem unrelated to the app's core functionality.
Finally, Google Play Protect scans should be conducted periodically to check for apps that have been detected as malware.


Comments