Over 5,300 GitLab servers exposed to zero-click account takeover attacks
Over 5,300 internet-exposed GitLab instances are vulnerable to CVE-2023-7028, a zero-click account takeover flaw GitLab warned about earlier this month.
The critical (CVSS score: 10.0) flaw allows attackers to send password reset emails for a targeted account to an attacker-controlled email address, allowing the threat actor to change the password and take over the account.
Although the flaw does not bypass two-factor authentication (2FA), it is a significant risk for any accounts not protected by this extra security mechanism.
The issue impacts GitLab Community and Enterprise Edition versions 16.1 before 16.1.5, 16.2 before 16.2.8, 16.3 before 16.3.6, 16.4 before 16.4.4, 16.5 before 16.5.6, 16.6 before 16.6.4, and 16.7 before 16.7.2.
GitLab released fixes in 16.7.2, 16.5.6, and 16.6.4, also backporting patches to 16.1.6, 16.2.9, and 16.3.7, on January 11, 2024.
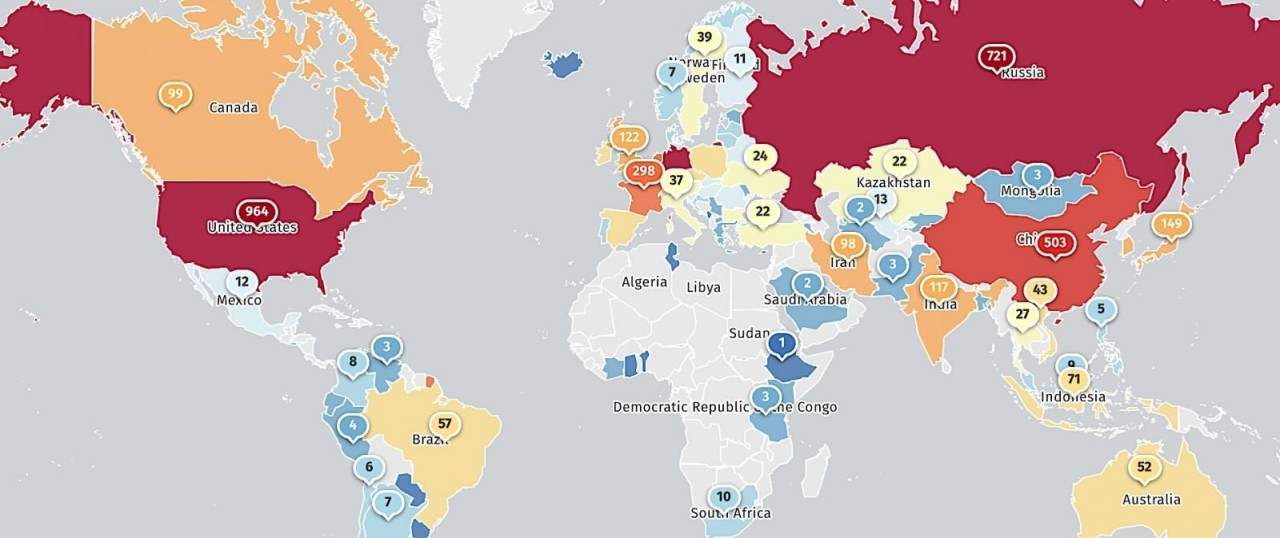
Today, 13 days after the security updates were made available, threat monitoring service ShadowServer reports seeing 5,379 vulnerable GitLab instances exposed online.
Based on GitLab's role as a software development and project planning platform and the type and severity of the flaw, these servers are at risk of supply chain attacks, proprietary code disclosure, API key leaks, and other malicious activity.
Shadowserver reports that most of the vulnerable servers are in the United States (964), followed by Germany (730), Russia (721), China (503), France (298), the U.K. (122), India (117), and Canada (99).
Those who haven't patched yet may have been compromised already, so using GitLab's incident response guide and checking for signs of compromise is critical.
GitLab previously shared the following detection tips for defenders:
Check gitlab-rails/production_json.log for HTTP requests to the /users/password path with params.value.email consisting of a JSON array with multiple email addresses.Check gitlab-rails/audit_json.log for entries with meta.caller.id of PasswordsController#create and target_details consisting of a JSON array with multiple email addresses.
Admins who find instances that have been compromised should rotate all credentials, API tokens, certificates, and any other secrets, in addition to enabling 2FA on all accounts and applying the security update.
After securing the servers, admins should check for modifications in their developer environment, including source code and potentially tampered files.
As of today, there have been no confirmed cases of active exploitation of CVE-2023-7028, but this shouldn't be interpreted as a reason to postpone taking action.


Comments