EDRSilencer red team tool used in attacks to bypass security
A tool for red-team operations called EDRSilencer has been observed in malicious incidents attempting to identify security tools and mute their alerts to management consoles.
Researchers at cybersecurity company Trend Micro say that attackers are trying to integrate EDRSilencer in attacks to evade detection.
"Our internal telemetry showed threat actors attempting to integrate EDRSilencer in their attacks, repurposing it as a means of evading detection."
by Trend Micro
"Muting" EDR products
Endpoint Detection and Response (EDR) tools are security solutions that monitor and protect devices from cyber threats.
They use advanced analytics and constantly updated intelligence to identify threats, both known and new, and respond automatically while sending a detailed report to defenders about the origin, impact, and spread of the threat.
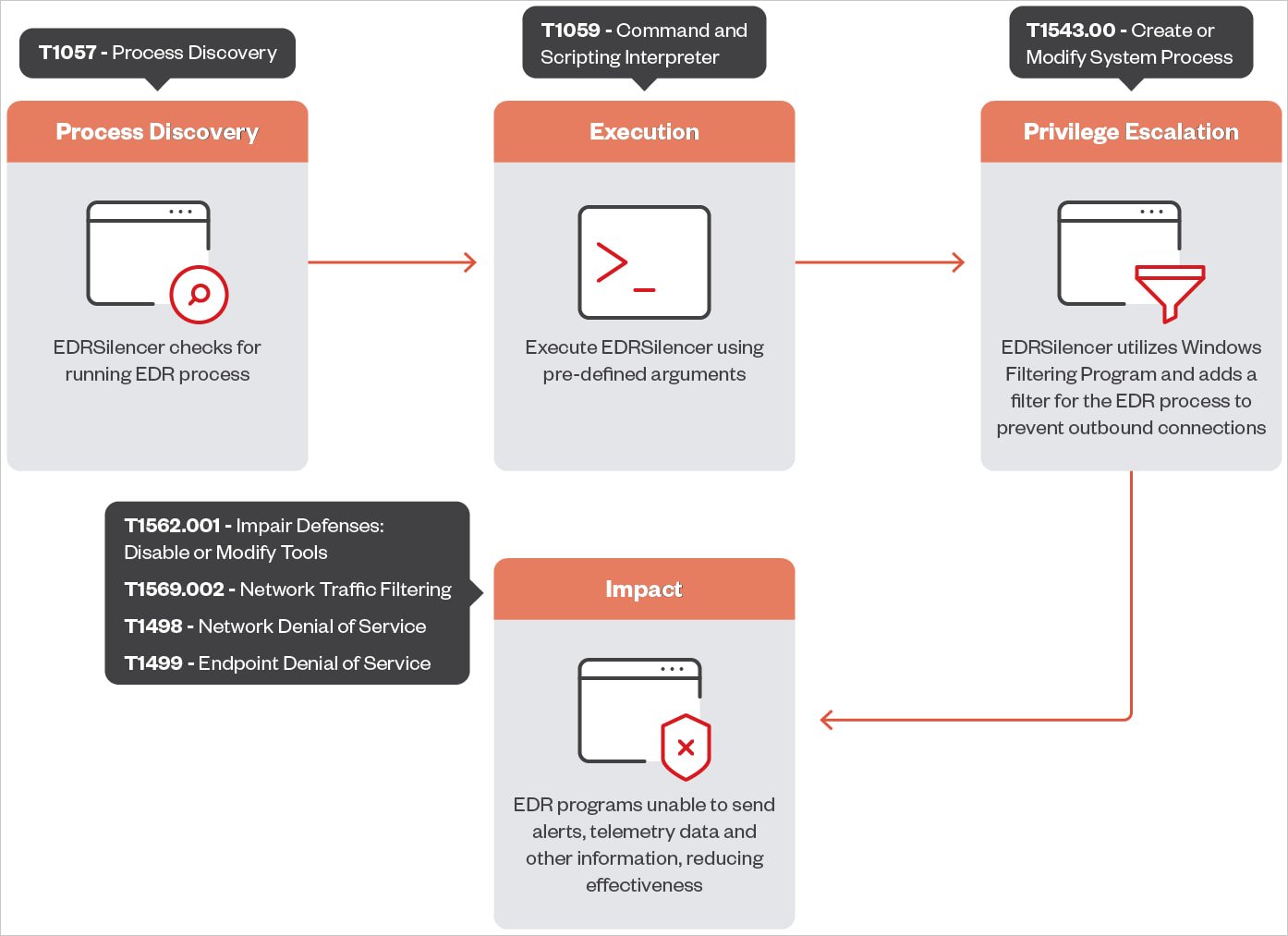
EDRSilencer is an open-source tool inspired by MdSec NightHawk FireBlock, a proprietary pen-testing tool, which detects running EDR processes and uses Windows Filtering Platform (WFP) to monitor, block, or modify network traffic on IPv4 and IPv6 communication protocol.
WFP is typically used in security products such as firewalls, antivirus, and other security solutions, and filters set in the platform are persistent.
With custom rules in place, an attacker can disrupt the constant data exchange between an EDR tool and its management server, preventing the delivery of alerts and detailed telemetry reports.
In its latest version, EDRSilencer detects and blocks 16 modern EDR tools, including:
- Microsoft Defender
- SentinelOne
- FortiEDR
- Palo Alto Networks Traps/Cortex XDR
- Cisco Secure Endpoint (formerly AMP)
- ElasticEDR
- Carbon Black EDR
- TrendMicro Apex One
TrendMicro's tests with EDRSilencer showed that some of the impacted EDR tools may still be able to send reports due to one or more of their executables not being included in the red team tool's hardcoded list.
However, EDRSilencer gives attackers the option to add filters for specific processes by providing file paths, so it is possible to extend the list of targeted processes to cover various security tools.
"After identifying and blocking additional processes not included in the hardcoded list, the EDR tools failed to send logs, confirming the tool's effectiveness," Trend Micro explains in the report.
"This allows malware or other malicious activities to remain undetected, increasing the potential for successful attacks without detection or intervention," the researchers say.
TrendMicro's solution to EDRSilencer is to detect the tool as malware, stopping it before it allows the attackers to disable security tools.
Additionally, researchers recommend implementing multi-layered security controls to isolate critical systems and create redundancy, use security solutions that provide behavioral analysis and anomaly detection, look for indicators of compromise on the network, and apply the principle of the least privilege.


.jpg)
Comments