Researchers expose Microsoft SCCM misconfigs usable in cyberattacks
Security researchers have created a knowledge base repository for attack and defense techniques based on improperly setting up Microsoft's Configuration Manager, which could allow an attacker to execute payloads or become a domain controller.
Configuration Manager (MCM), formerly known as System Center Configuration Manager (SCCM, ConfigMgr), has been around since 1994 and is present in many Active Directory environments, helping administrators manage servers and workstations on a Windows network.
It has been the object of security research for more than a decade as an attack surface [1, 2, 3] that could help adversaries gain administrative privileges on a Windows domain.
At the SO-CON security conference today, SpecterOps researchers Chris Thompson and Duane Michael announced the release of Misconfiguration Manager, a repository with attacks based on faulty MCM configurations that also provides resources for defenders to harden their security stance
"Our approach extends beyond cataloging the tactics of known adversaries to include contributions from the realm of penetration testing, red team operations, and security research," the SpecterOps explain.
The two researchers say that MCM/SCCM is not easy to set up and that many of the default configurations leave room for attackers to take advantage.
Getting domain control
In a blog post, Michael illustrates that the most common and damaging misconfiguration researchers see in their engagements are network access accounts (NAA) with too many privileges.
Referring to MCM/SCCM, the researcher notes that "it's overwhelming to configure, and a novice or unknowing administrator may choose to use the same privileged account for all of the things."
During their work, they encountered one scenario that followed the path from compromising the SharePoint account of a standard user to becoming a domain controller, all due to a misconfigured MCM deployment of MCM with overprivileged NAAs.
In another example, Michael says that Configuration Manager sites could enroll domain controllers as clients, which introduces the risk of remote code execution if the site hierarchy is not properly set up.
To demonstrate the risk of a misconfigured MCM/SCCM deployment even further, the researcher outlined an experience where the team was able to get into the central administration site (CAS) database of MCM/SCCM and grant themselves a full administrator role.
From there, they could compromise the environment further by using Configuration Manager to execute on a payload previously planted on a network share on a domain client.
Attack and defense methods
The Misconfiguration Manager repository created by Chris Thompson, Garrett Foster, and Duane Michael aims to help administrators better understand Microsoft's tool and "simplify SCCM attack path management for defenders while educating offensive professionals on this nebulous attack surface."
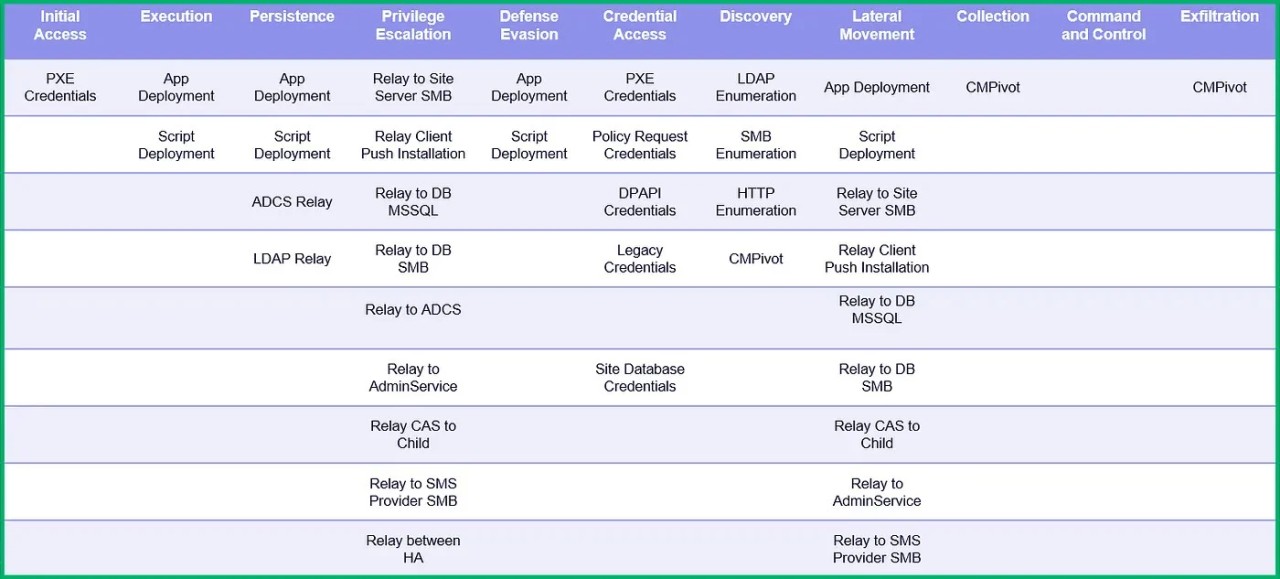
Currently, the repository describes 22 techniques that could be used to attack MCM/SCCM directly or to leverage it in post-exploitation stages.
Depending on the environment, the techniques described could allow access to credentials (CRED), elevate privileges (ELEVATE), perform reconnaissance and discovery (RECON), or gain control of the MCM/SCCM hierarchy (TAKEOVER).
For each attack method, the researchers also provide information to protect the environment against each of the presented offensive techniques.
Defense actions are split into three categories:
- PREVENT: configuration changes that directly mitigate or impact an attack technique
- DETECT: guidance and strategies for detecting various attack techniques
- CANARY: detection strategies based on deception, using features that attackers commonly abuse
Considering that it is widely adopted and must be installed in an Active Directory domain, MCM/SCCM can decrease a company's security posture if configured improperly, a task fit for an experienced administrator.
Although tested by the creators of Misconfiguration Manager, administrators are strongly advised to test the defense methods provided in the repository before implementing them in a production environment.


Comments